
Guide to Data Security and Privacy in Microsoft Fabric
Murthy
6th Aug 2025
Talk to our cloud experts
Subject tags
Microsoft Fabric, as a Software-as-a-Service (SaaS) analytics platform, embeds enterprise-grade security directly into the architecture. Its design ensures strict control over access, encryption, compliance, and data protection across multi-tenant environments.
Key Takeaways
- It features real-time threat detection, automated responses, and access control via RBAC and MFA.
- Network security is strengthened with Private Links, Managed Endpoints, and Conditional Access.
- Data resilience is guaranteed with geo-redundant storage and disaster recovery options.
- Supports compliance with global regulations like GDPR and HIPAA.
What is Data Security in Microsoft Fabric?
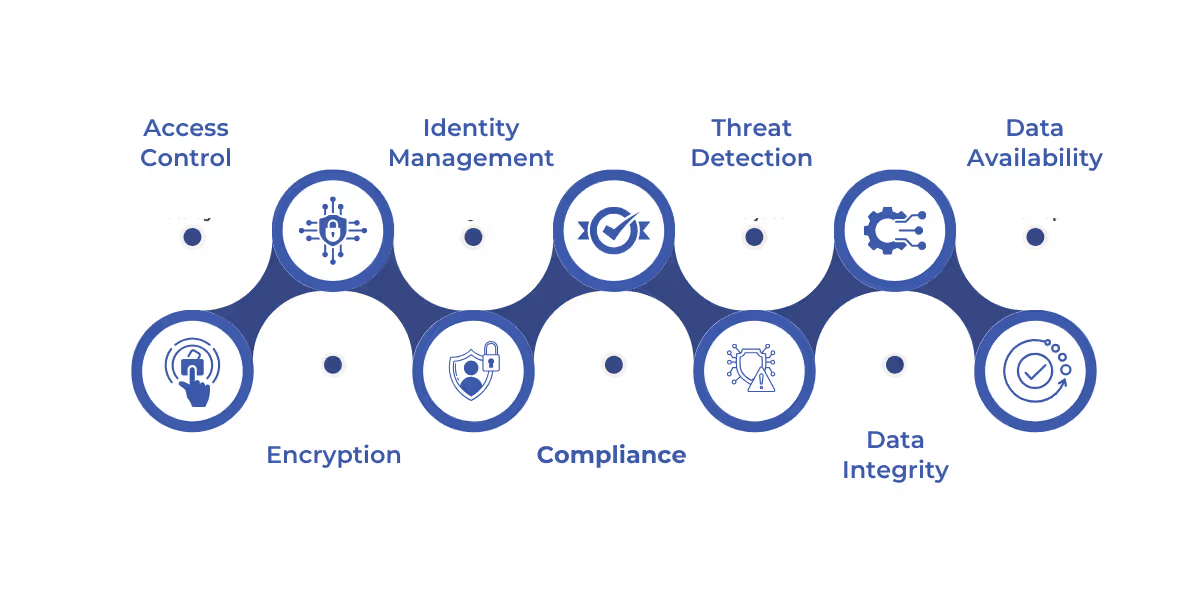
Data security in Microsoft Fabric ensures the protection of data from unauthorized access, alteration, or loss, maintaining its confidentiality, integrity, and availability.
It employs encryption, access control, and compliance measures to safeguard both structured and unstructured data.
- Access Control: Role-based access and policies via Azure Active Directory and RBAC.
- Encryption: AES-256 for data at rest, TLS 1.2 for data in transit.
- Identity Management: Integration with Microsoft Entra ID and multi-factor authentication (MFA).
- Compliance: Supports GDPR, HIPAA, and other global regulations.
- Threat Detection: Real-time monitoring and automated responses using Azure Sentinel.
- Data Integrity: Ensures data remains intact through strong authentication.
- Data Availability: High availability and disaster recovery features.
To ensure that only authorized users have access to critical resources, Microsoft Fabric incorporates a robust identity and access management framework.
Identity and Access Management (IAM)
IAM in Microsoft Fabric governs who can access resources and under what conditions, using centralized identity controls and policy enforcement.
Microsoft Entra ID Integration:
All access to Fabric is authenticated via Entra ID, providing centralized identity and access management across devices and networks. This ensures consistent enforcement of login policies and session security.
Multi-Factor Authentication (MFA):
MFA policies can be enforced through Conditional Access to require two or more verification methods. This prevents unauthorized access from compromised credentials, especially in sensitive environments like R&D and finance.
Role-Based Access Control (RBAC):
Fabric workspaces use granular roles (Admin, Member, Contributor, Viewer) to restrict access by role. Permissions are scoped to workspace items, and user privileges limit SQL/DAX queries.
To further safeguard data, Microsoft Fabric employs advanced network security and access controls to manage both internal and external data traffic securely.
Network Security and Access Controls
Fabric secures all internal and external data traffic using network isolation, private connectivity, and conditional access mechanisms.
Inbound Security:
- Private Links: Enforces VNet-only access by disabling public ingress, isolating workspace resources such as Notebooks and Lakehouses.
- Conditional Access: Configure policies to restrict access by IP ranges, country, device compliance, or require MFA. Access is blocked if conditions are not met.
Outbound Security:
- Trusted Workspace Access: Enables Fabric workspaces to securely access Azure Data Lake Gen2 accounts without opening public endpoints.
- Managed Private Endpoints and Virtual Networks: Support secure, private connections to external sources like Azure SQL or Cosmos DB, removing exposure to public IP ranges.
- Service Tags: Allow outbound traffic to Fabric from controlled sources like Azure SQL VMs without requiring data gateways.
- IP Allowlists: Useful for non-Azure data sources or legacy systems, allowing selective IP access for Fabric workloads.
Also Read: Azure Cloud Modernization Strategies for the Future
With encryption being a cornerstone of data protection, Microsoft Fabric ensures that all data, both at rest and in transit, is securely encrypted using industry-leading protocols.
Encryption and Key Management
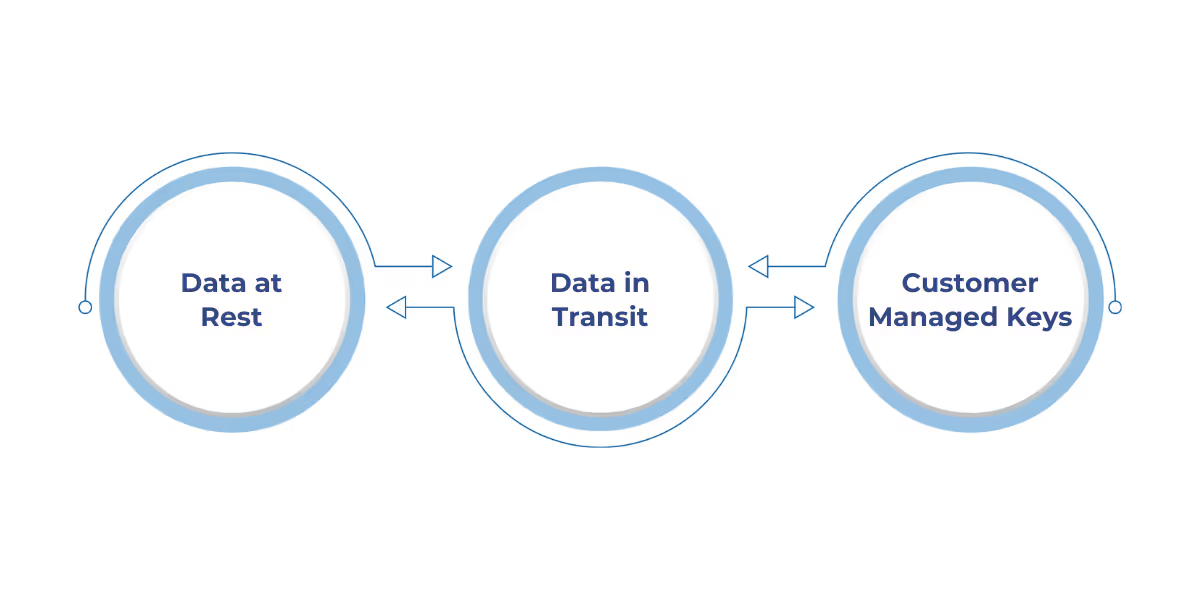
Microsoft Fabric encrypts data both at rest and in transit using enterprise-grade standards, with optional customer-managed key controls.
- Data at Rest: All data stored in OneLake is encrypted using AES-256. Data resides in the home region or specified geo-regions to meet data residency requirements.
- Data in Transit: TLS 1.2 or higher is enforced for all communication, including between services and to/from clients. No communication is sent in plaintext.
- Customer Managed Keys (CMKs): Optionally, organizations can configure Azure Key Vault to bring their own encryption keys, allowing full control over key lifecycle, rotation, and access.
In addition to encryption, Microsoft Fabric integrates comprehensive governance tools that enforce compliance with global data privacy regulations and enhance data management.
Data Governance and Privacy Controls
Fabric implements layered governance through sensitivity labels, policy-based controls, and data access scoping to support compliance with global data regulations.
- Sensitivity Labels and Information Protection: Labels such as “Confidential” or “Highly Confidential” are inherited from Microsoft Purview and automatically propagate across supported formats (PBIX, Excel, PowerPoint).
- Access Scoping:
- Row-Level Security (RLS): Restricts SQL/DAX query results based on user identity.
- Column-Level Security (CLS) and Object-Level Security (OLS): Ensure users only access authorized fields and objects in the schema.
- Data Minimization: Fabric enables fine-grained control over which data is ingested, stored, and accessed, reducing unnecessary exposure and improving compliance alignment.
- Multi-Geo Support: Enables tenant-level data placement in specific Azure geographies. Only metadata and orchestration services may reside in the home region, while query execution and storage stay geo-localized.
Microsoft Fabric also uses real-time monitoring and automated threat detection to ensure the security of all data operations across the platform.
Threat Detection and Operational Monitoring
Microsoft Fabric integrates monitoring and automated threat response capabilities to maintain operational security across workloads.
- Security Monitoring via Azure Sentinel: Real-time telemetry from Fabric services is ingested into Sentinel for SIEM analysis, correlation rules, and incident alerting.
- Automated Responses: On detection of suspicious behavior or policy violations, Fabric can trigger pre-defined actions such as session termination, credential revocation, or data quarantining.
- Audit Logs: Track user-level activity, including access to sensitive items, failed login attempts, and data modification actions. Export logs to Microsoft Sentinel, Log Analytics, or external SIEM tools for compliance.
Ensuring the continuity of operations, Microsoft Fabric includes built-in resiliency and data recovery features to minimize downtime in the event of a disaster.
Resilience and Data Recovery
Fabric ensures high availability and data recoverability through geo-redundant storage and infrastructure resilience features.
- Regional Availability Zones: Fabric relies on Azure’s fault domain architecture for zone-resilient data and service continuity.
- Disaster Recovery: Supports failover and recovery procedures aligned with organizational continuity plans.
- Backups: While abstracted from the user, Fabric ensures recovery points are available internally to Microsoft support for incident response.
Finally, Microsoft Fabric offers detailed governance and administrative controls, providing the flexibility to manage security policies and monitor usage efficiently.
Governance and Administration
Administrative capabilities in Fabric allow policy delegation, usage monitoring, and organizational security posture management.
- Scoped Admin Roles: Grant administrative control per workspace, capacity, or domain. Helps avoid over-privileging and centralizes audit responsibility.
- Monitoring Tools: Track capacity usage, data refresh metrics, and API activity to detect anomalies or abuse.
- Compliance Auditing: Use Microsoft Purview for classification, lineage tracking, and data cataloging across Fabric and linked services.
Summary of Fabric Security Capabilities
How WaferWire Drives Digital Transformation for Your Business
WaferWire helps businesses optimize cloud infrastructure, implement efficient strategies, and use data analytics to enhance operations and growth. Here's how we can help:
- Cloud Services: Custom cloud solutions that scale with your business needs, ensuring smooth migration and resource management.
- Artificial Intelligence: Solutions that automate tasks, improve decision-making, and cut operational costs.
- Data Analytics: Transform data into clear insights for better performance and informed decision-making.
Tailored Solutions for Every Business
Whether you're a large enterprise or a smaller business, WaferWire provides solutions tailored to your specific needs. We work with industries such as retail, manufacturing, financial services, and utilities.
Your Strategic Partner in Digital Transformation
WaferWire offers full support from strategy development to implementation, delivering practical solutions that drive results. Contact us to enhance your business operations.
Conclusion
Microsoft Fabric prioritizes your data security with encryption, access control, and real-time threat detection. By incorporating identity management, RBAC, and global compliance, it ensures your data is always protected and secure.
Ongoing monitoring and adherence to best practices are key to maintaining this security. By using these features effectively, businesses can safeguard their data and meet compliance requirements.
At WaferWire, we assist with the implementation and optimization of Microsoft Fabric’s security features. Contact us today for help with setup, compliance, and custom configurations to secure your data.
FAQs
Q: How does Microsoft Fabric ensure secure data transfer?
A: Microsoft Fabric encrypts all data in transit using TLS 1.2 or higher, securing the communication channels between clients and servers. This encryption ensures that data cannot be intercepted or tampered with during transfer. It helps protect sensitive business information in transit across networks.
Q: Can I control access to individual data items in Microsoft Fabric?
A: Yes, Microsoft Fabric allows you to control access at a granular level with row-level security (RLS), column-level security (CLS), and object-level security (OLS). These controls enable you to define who can access specific data based on user roles and permissions. This ensures sensitive data is only accessible to authorized users.
Q: Does Microsoft Fabric support hybrid cloud environments?
A: Microsoft Fabric supports hybrid cloud deployments, enabling integration with on-premises systems and other cloud services. It uses secure data gateways and private endpoints to connect on-premises data sources to the cloud securely. This flexibility allows businesses to combine cloud and on-premises resources seamlessly.
Q: How does Microsoft Fabric handle regulatory compliance?
A: Microsoft Fabric adheres to global standards such as GDPR, HIPAA, and more, ensuring data privacy and security. It provides built-in compliance features, certifications, and tools to help organizations meet regulatory requirements. This helps businesses maintain data protection while operating in regulated industries.
Q: Can Microsoft Fabric scale to meet growing business needs?
A: Yes, Microsoft Fabric is designed to scale dynamically based on business requirements. It offers flexible cloud infrastructure that adjusts to increased data volumes and processing demands. This scalability ensures that businesses can grow without worrying about infrastructure limitations.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)














