Key Cloud Compliance Certifications for Healthcare Data Modernization 2025
Harish
31st Oct 2025

Talk to our cloud experts
Subject tags
Healthcare modernization is increasingly shifting PHI to public clouds, a trend that coincides with the accumulation of audits, BAAs, and third-party reviews. Meanwhile, CISOs, compliance officers, and cloud architects also need a standard playbook for shared responsibility, as without it, projects slow down and evidence becomes disputed.
Cloud certifications provide that playbook by defining scope, control tests, evidence formats, and assessment cadence across provider and customer roles.
In this guide, we explain what certifications are, why they matter now, and how they fit into an operating model you can run at speed.
Key Takeaways
- Healthcare organizations require certifications such as ISO 27001, SOC 2, and HITRUST to ensure HIPAA and GDPR compliance in cloud environments.
- AI, blockchain, and confidential computing are enhancing compliance by automating checks and securing sensitive data.
- Transitioning to continuous, automated monitoring improves real-time compliance and reduces audit burden.
- Cloud providers must offer encryption, secure connectivity, and monitoring tools to support compliance.
- Certifications streamline procurement, architecture, and contract negotiations, lowering risks and improving efficiency.
Key Compliance Frameworks and How They Fit into An Operating Model
How certifications fit the operating model
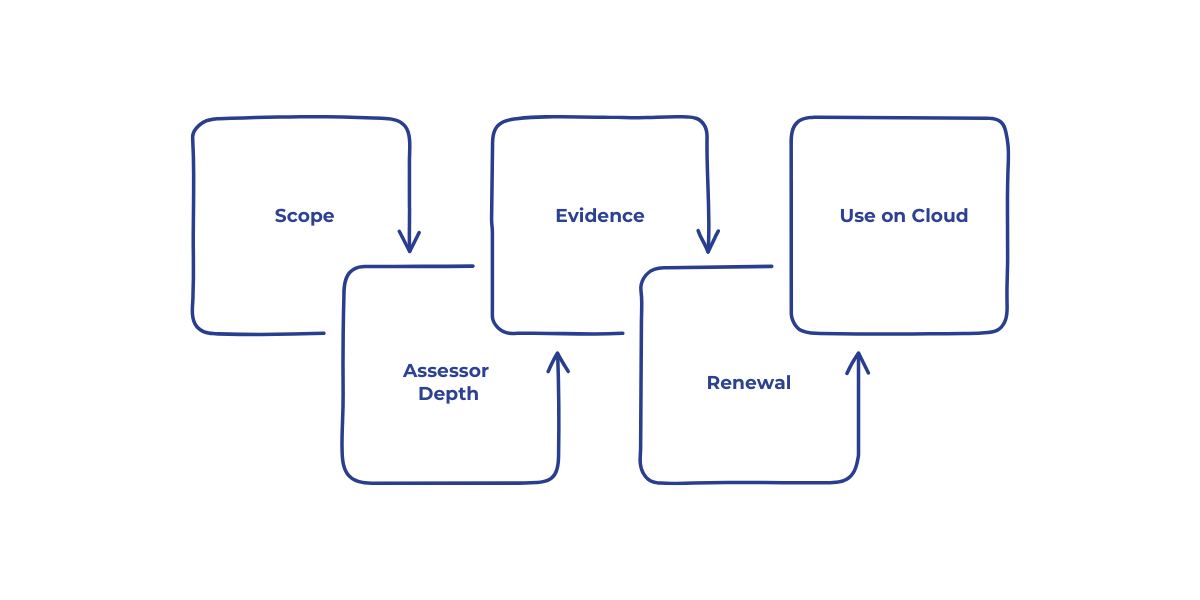
Begin by establishing agreement on the boundary, the assessor, the evidence, and the renewal rhythm.
- Scope: The services, regions, and features that sit inside the audit boundary.
- Assessor depth: Self-attestation, third-party attestation, or accredited certification.
- Evidence: Control mapping, test procedures, artifacts, and a continuous monitoring feed.
- Renewal: Point-in-time certification, continuous assurance, and any interim surveillance.
- Use on cloud: Inherit provider controls, provide customer controls, and document shared ones.
Top Compliance Frameworks
Companies prefer recognized frameworks because they transform security policies into auditable controls and evidence that partners can trust.
You can anchor program management with ISO to set scope, risk treatment, privacy roles, and documentation. NIST can be used to specify technical controls, testing, and automation. Let’s understand each of these frameworks better:
1. ISO 27000 family
Use ISO to anchor governance, privacy, and cloud-specific controls that auditors and partners recognize.
- ISO 27001 for ISMS governance and risk management.
- ISO 27002 control guidance with cloud-specific references.
- ISO 27017 cloud control guidance across provider and customer roles.
- ISO 27018 protection of personal data in public cloud.
- ISO 27701 privacy information management is linked to GDPR and state privacy laws.
How to apply
- Stand up an ISMS with a defined scope and a repeatable risk method.
- Map provider attestations to Annex A controls for inheritance.
- Use a Statement of Applicability to track included and excluded controls.
- Run internal audits and management reviews on a fixed cadence.
2. NIST 800 and related models
Use NIST for technical depth, precise control of wording, and machine-readable catalogs that support automation.
- NIST SP 800-53 rev.5 for identity, logging, crypto, and supply chain controls.
- NIST SP 800-171 for controlled unclassified information in partner networks.
- NIST CSF 2.0 to measure program maturity across Identify, Protect, Detect, Respond, and Recover.
- OSCAL formats for machine-readable catalogs and evidence to automate assessments.
How to apply
- Select baselines for clinical, research, or payer integrations.
- Encode policies as code using OPA or native cloud policy engines.
- Store test results, tickets, and logs as evidence linked to control IDs.
Also Read: Healthcare Data Privacy and Security Evolution in 2025
With the growing importance of standardized frameworks, HITRUST plays a central role in streamlining healthcare data compliance.
Role of HITRUST in Healthcare Data Modernization
HITRUST CSF consolidates ISO, NIST, HIPAA, and state requirements into a single assessed framework with “inheritance” from cloud providers. It is the most common route to a single assertion accepted by payers and partners.
What the CSF brings
- HITRUST e1, i1, r2 assessment types with rising rigor and assurance
- Crosswalks to HIPAA Security Rule, NIST 800-53, ISO 27001, PCI, and state privacy laws
- Continuous Assurance options that push control, health, and evidence freshness
Evidence of impact
How to implement
- Choose the assessment type based on data sensitivity and partner expectations.
- Inherit cloud controls where available, then prove customer-side controls.
- Use the MyCSF platform to track corrective actions and evidence cycles.
Certifications significantly impact the cloud adoption process, offering critical advantages in procurement, architecture, and operations.
What is the Impact of Certifications on Cloud Adoption
Certifications often shorten third-party risk reviews, allocate PHI workloads, and reduce the need for custom questionnaires.
They do not remove the need for customer-side security, but they give a verified foundation.
Where certifications move the needle:
- Procurement: Faster approvals with documented scope and test results
- Architecture: Clear patterns for encryption, identity, logging, and network isolation
- Operations: Defined metrics for control health and incident response readiness
- Contracts: Simpler clauses for HIPAA BAA, data residency, and breach reporting
Context from recent breaches:
Programs now ask for stronger MFA, least privilege, and documented control tests as table stakes.
Emerging Compliance Trends in Healthcare Cloud

Healthcare organizations are moving beyond point-in-time audits towards continuous evidence, policy-as-code, and risk scoring driven by real-time signals. AI, machine learning, and cryptography are becoming key parts of everyday operations, improving both compliance and data security.
Here's a look at the trends driving change:
1. AI and Machine Learning in Healthcare Compliance
Machine learning is essential for improving data security and compliance in healthcare. It helps detect irregularities in identity permissions and identifies anomalous access, significantly reducing the need for manual checks.
Key Actions:
- Identity and Access Management (IAM): Use ML models to monitor and analyze behavior patterns. Automatically flag any unauthorized access, improving response times and reducing security risks.
- Automated Audit Processes: Large language models (LLMs) can assist in automating audit tasks, such as triaging evidence and mapping incidents to compliance controls. This reduces manual work and accelerates compliance reviews.
- Model Lineage Documentation: Ensure that all AI processes, model decisions, datasets, and prompts are documented as part of your control evidence. This enhances transparency and ensures compliance with standards like HIPAA.
2. Blockchain for Enhanced Healthcare Compliance
Blockchain offers a secure, immutable way to create transparent audit trails across multiple stakeholders in the healthcare ecosystem, including payers, labs, and providers.
Key Actions:
3. Confidential Computing and Data Security Posture
Confidential computing enables secure processing of sensitive data, such as Protected Health Information (PHI), using hardware-enforced enclaves. This ensures that PHI remains encrypted and protected, even during processing.
Key Actions:
- Secure Data Processing: Adopt confidential computing technologies to process PHI within secure enclaves. This is essential for maintaining compliance in multi-cloud or hybrid environments.
- Data Security Posture Management (DSPM): Use DSPM tools to continuously monitor, classify, and track sensitive data across your cloud infrastructure. Ensure that all data is encrypted and managed according to strict security policies to meet regulatory standards like HIPAA and GDPR.
When selecting a cloud provider, it is essential to ensure they meet the necessary compliance requirements for a secure healthcare data environment.
Choosing the Right Cloud Provider for Healthcare Compliance
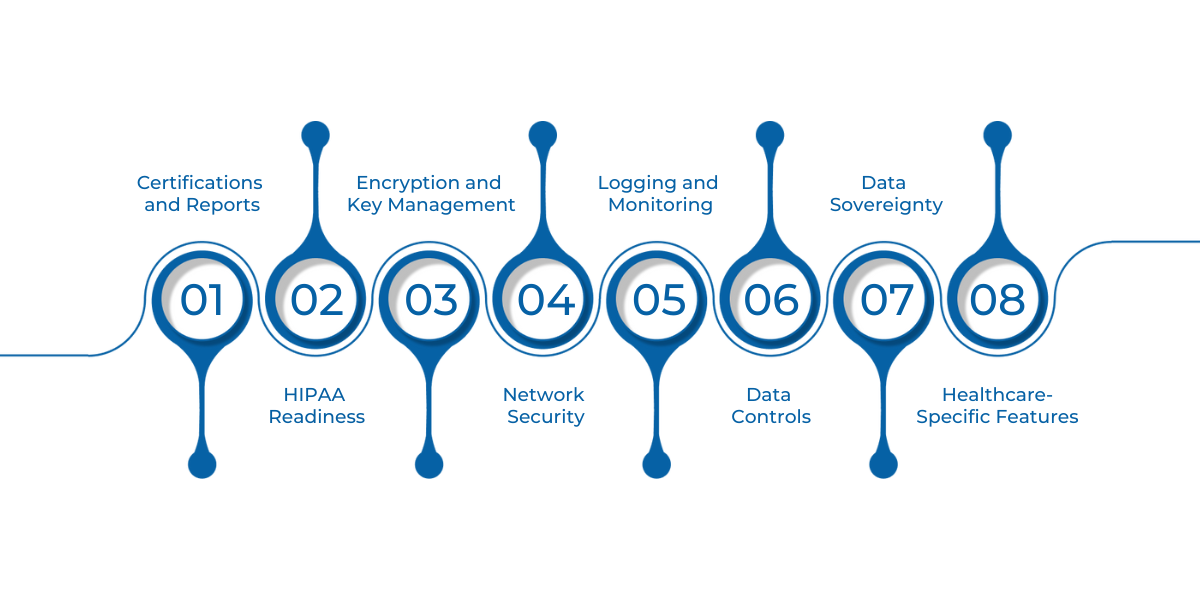
When selecting a cloud provider for your healthcare data, it’s crucial to ensure they meet the necessary compliance standards and provide the right tools for secure and efficient data management. The following checklist outlines key criteria to consider:
- Certifications and Reports: Ensure the provider holds relevant certifications like ISO 27001, ISO 27017, ISO 27018, ISO 27701, SOC 2, FedRAMP (if needed), and HITRUST inheritance catalogs.
- HIPAA Readiness: Confirm the provider supports HIPAA and can provide a Business Associate Agreement (BAA). Look for clear documentation on services eligible for handling PHI and customer guides to navigate compliance.
- Encryption and Key Management Check for Customer-Managed Encryption Keys (CMEK) or Hardware Security Module (HSM) options. Ensure key rotation APIs and envelope encryption are the default settings.
- Network Security: Verify private connectivity, service endpoints, egress controls, and DNS policy to protect your data in transit.
- Logging and Monitoring: Look for immutable storage options, long data retention periods, and the ability to export logs to a SIEM system. Ensure support for workload tracing to enhance auditability.
- Data Controls: Ensure the provider offers Data Security Posture Management (DSPM), Data Loss Prevention (DLP), tokenization, and object lock features.
- Data Sovereignty: Assess the provider’s region coverage, residency commitments, and transparency around data access and sovereignty.
- Healthcare-Specific Features: Check for healthcare accelerators like reference architectures, FHIR services, and audit packs that align with healthcare data requirements.
How to Compare Providers
- Map Your Architecture: Align your existing architecture with each provider’s list of assessed services. Identify which services support your needs for compliance and security.
- Identify Control Gaps: List any gaps in controls you must manage yourself. Ensure the provider offers tools to help fill those gaps.
- Request Inheritance Matrices: Ask for evidence and inheritance matrices to verify audit handoffs and ensure compliance is maintained across both sides of the model.
As compliance needs evolve, adopting a continuous compliance model is key to staying ahead in a dynamic cloud ecosystem.
How to Ensure Continuous Compliance
To maintain continuous compliance in a dynamic cloud environment, it's essential to treat compliance controls as code and evidence as data.
This approach integrates automation and continuous monitoring into your compliance strategy, enabling you to adapt quickly to regulatory changes.
Program steps
- Policy as code: Azure Policy, AWS Config, GCP Policy Controller, plus OPA Gatekeeper
- IaC guardrails: Terraform or Bicep modules with built-in controls and tests
- Continuous control monitoring: Near-real-time evaluation and ticket creation
- Evidence automation: Pull logs, screenshots, and configs into a system of record
- Drift response: Auto-remediate where safe, quarantine where risky
- Audit-ready reporting: OSCAL exports and mapped controls for ISO, NIST, and HITRUST.
Conclusion
As healthcare data modernization accelerates, maintaining compliance with regulations like HIPAA and GDPR is crucial. Advanced technologies like AI, blockchain, and confidential computing further enhance compliance by automating checks, tracking data access, and securing sensitive information.
Healthcare organizations must shift from point-in-time audits to continuous, automated monitoring, collecting evidence, and tracking compliance drift in real-time. This proactive approach reduces audit burden and minimizes risk.
At WaferWire, we understand the unique compliance challenges healthcare organizations face. With our deep expertise in cloud services, AI, and data analytics, we deliver customized solutions that ensure ongoing compliance and enhance security.
Partner with WaferWire today to streamline your healthcare data compliance and safeguard your cloud infrastructure for the future.
FAQs
Q: What is the role of automated evidence collection in cloud compliance?
A: Automated evidence collection simplifies audits by continuously gathering data such as logs and configurations. This ensures that compliance is always ready for review, reduces manual work, and speeds up incident response.
Q: Can healthcare organizations use AI to reduce compliance workload?
A: Yes, AI can automate tasks like auditing, detecting anomalies, and mapping incidents to compliance controls. It reduces manual effort, accelerates audits, and ensures continuous compliance monitoring.
Q: How does continuous monitoring improve healthcare data security?
A: Continuous monitoring helps detect security breaches or compliance drift in real time. By automating this process, healthcare organizations can act quickly, minimizing risk and ensuring ongoing protection for sensitive data.
Q: What impact do certifications like SOC 2 have on cloud security for healthcare?
A: SOC 2 certifications ensure that a cloud provider meets stringent security, availability, and confidentiality standards. These certifications provide healthcare organizations with confidence that their cloud infrastructure is secure and compliant with industry standards.
Q: How do I choose the right cloud provider for healthcare compliance?
A: When selecting a cloud provider, ensure they meet HIPAA requirements, offer robust encryption, and have relevant certifications like ISO 27001 and HITRUST. Verify they provide tools for continuous monitoring and control management.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)