Healthcare Data Privacy and Security Evolution in 2025
Sai P
2nd Sept 2025

Talk to our cloud experts
Subject tags
In 2025, healthcare is more connected than ever, powered by telemedicine, wearable devices, and AI-driven diagnostics. This digital transformation has made data privacy in healthcare a critical priority, not just for regulatory compliance but for protecting patient trust.
Cyberattacks on hospitals, ransomware targeting medical devices, and complex global privacy laws are forcing healthcare organizations to rethink security from the ground up. New technologies like AI-powered threat detection, blockchain records, and zero-trust architectures are reshaping how sensitive patient data is stored, shared, and safeguarded.
This blog explores how data privacy in healthcare is evolving in 2025, the challenges it faces, and the strategies needed to secure patient information without slowing innovation.
Key Takwaways :
- Healthcare data breaches are increasingly sophisticated, making proactive security a must.
- Key regulations like HIPAA, GDPR, and CCPA demand robust compliance strategies.
- Modern security technologies (AI, encryption, zero trust) are essential defense layers.
- Cloud platforms, when implemented with the right security controls, enhance privacy and scalability.
- Future trends point toward AI-driven monitoring, real-time compliance tracking, and patient-controlled health data.
Understanding Data Privacy in Healthcare
Healthcare data privacy goes beyond merely locking files behind passwords. It encompasses the policies, processes, and technologies that ensure patient information is accessed, shared, and stored responsibly. In 2025, data privacy in healthcare is more critical than ever due to the increasing volume, variety, and velocity of data generated from electronic health records (EHRs), medical imaging, wearable devices, and telehealth platforms.
Distinguishing Privacy and Security
While often used interchangeably, privacy and security serve different purposes:
- Privacy refers to controlling who has access to data and how it is used. For example, a patient’s genomic data should only be accessible to authorized healthcare professionals and not shared without consent.
- Security ensures that data is protected from unauthorized access, breaches, or corruption. Security measures include encryption, intrusion detection systems, and multi-factor authentication.
Types of Sensitive Healthcare Data
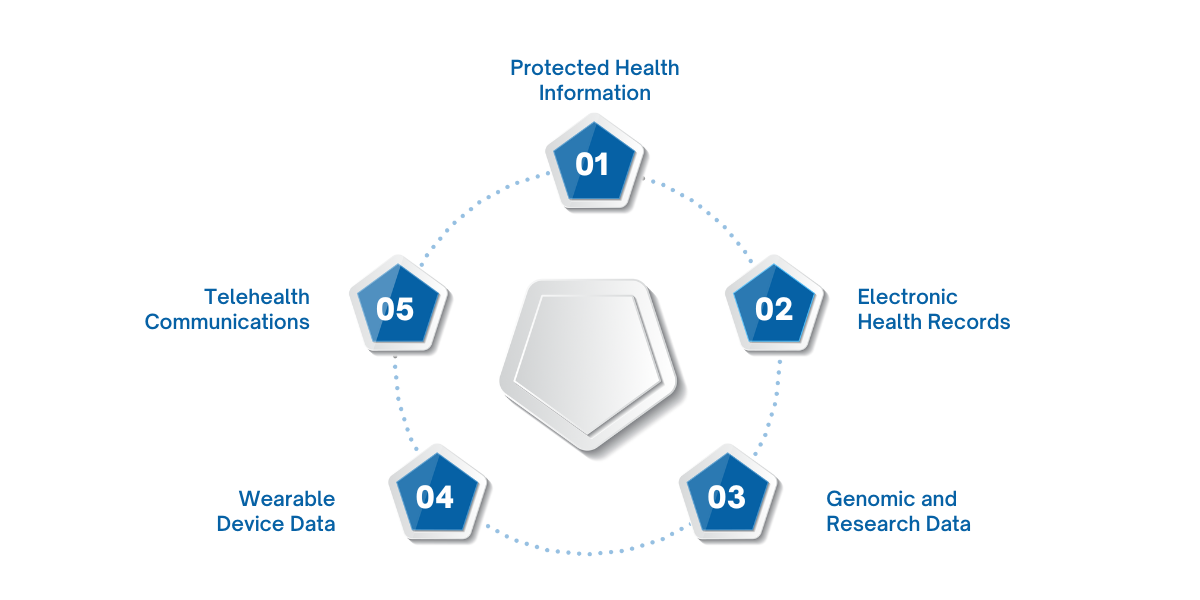
Healthcare organizations manage a wide array of sensitive data, including:
- Protected Health Information (PHI) – Personal identifiers, medical histories, lab results.
- Electronic Health Records (EHRs) – Comprehensive patient care documentation.
- Genomic and Research Data – Highly sensitive data requiring strict access control.
- Wearable Device Data – Continuous monitoring information such as heart rate, glucose levels, and activity metrics.
- Telehealth Communications – Video consultations, messages, and remote monitoring data.
Patients expect their data to be handled with care. Breaches or misuse can erode confidence in providers, reduce engagement, and have legal consequences. As technology evolves, maintaining trust requires proactive privacy strategies that combine compliance, robust security, and transparent data usage practices.
By understanding these fundamentals, healthcare organizations can lay the groundwork for implementing advanced privacy measures and technologies that keep patient data safe, while still enabling innovation in care delivery.
Key Regulations and Compliance Frameworks in 2025
The regulatory landscape for data privacy in healthcare has evolved significantly to keep pace with emerging technologies and cyber threats. Compliance is no longer just about avoiding penalties; it’s a critical component of patient trust and operational resilience. In 2025, healthcare organizations must navigate a complex web of federal, state, and international regulations while adopting best practices for data governance.
HIPAA Updates and Modernization
The Health Insurance Portability and Accountability Act (HIPAA) remains the cornerstone of healthcare privacy in the United States. Recent updates in 2025 emphasize:
- Enhanced patient rights to access, correct, and control their health data.
- Stricter breach notification timelines, requiring organizations to report incidents faster.
- Guidance for cloud-based storage and AI-driven analytics to ensure compliance in modern digital infrastructures.
HIPAA now encourages proactive risk assessment and integrates more closely with other federal standards, creating a unified compliance approach.
HITECH Act and Health IT
The Health Information Technology for Economic and Clinical Health (HITECH) Act continues to drive digital adoption in healthcare. In 2025, HITECH focuses on:
- Incentivizing secure, interoperable EHR systems.
- Promoting real-time auditing of electronic health data.
- Supporting telehealth compliance frameworks to meet privacy and security standards.
Global Influence: GDPR and Beyond
Global privacy laws such as the General Data Protection Regulation (GDPR) influence U.S. healthcare providers who handle international patient data. Key elements include:
- Explicit patient consent for data collection and processing.
- Right to data portability and erasure.
- Mandatory breach notifications within 72 hours of detection.
State-level regulations, like California’s CCPA and CPRA, also set stricter privacy expectations for patient data, particularly regarding consumer rights and vendor accountability.
ISO 27001 and HITRUST Certification
For enterprise healthcare systems, compliance with international standards adds another layer of assurance:
- ISO 27001 provides a framework for implementing a comprehensive information security management system (ISMS).
- HITRUST CSF combines multiple standards, including HIPAA, ISO, and NIST, to simplify certification and reduce audit complexity.
With increasing adoption of cloud solutions, AI-driven analytics, and connected medical devices, organizations must integrate compliance into their operational workflows. Automated monitoring, AI-assisted auditing, and secure cloud migrations help maintain adherence to these regulations while reducing operational overhead.
By understanding the evolving regulatory environment, healthcare providers can mitigate risk, protect patient data, and ensure trust across the entire care ecosystem.
Top Threats to Healthcare Data Privacy in 2025
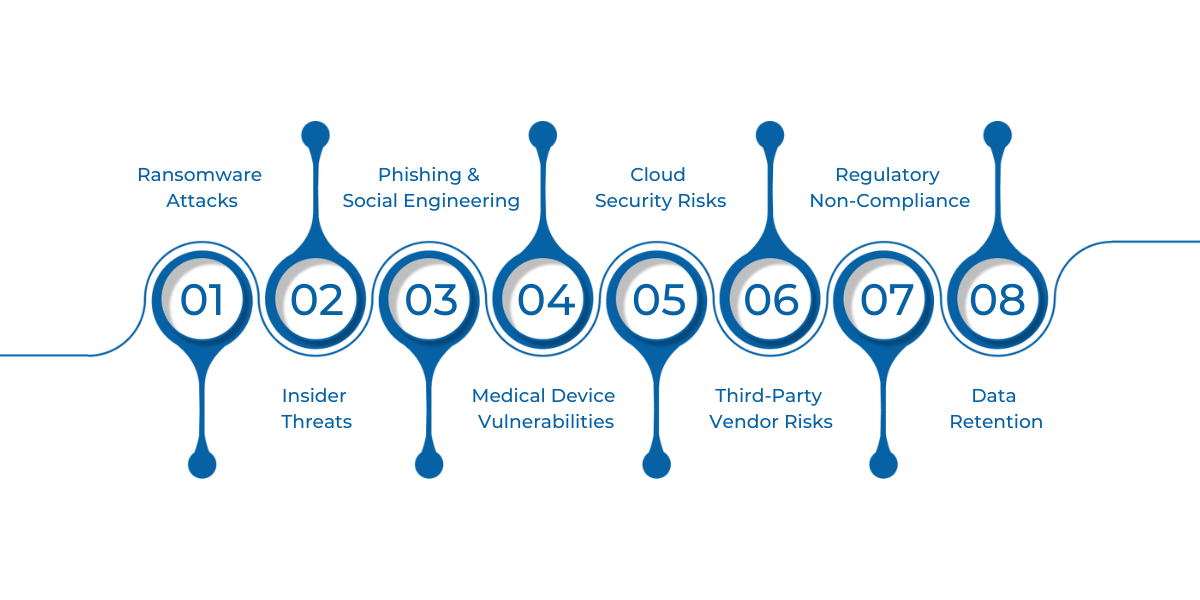
As healthcare organizations increasingly digitize and interconnect their systems, they face a growing array of cybersecurity threats. In 2025, these threats have become more sophisticated, frequent, and impactful. Understanding these risks is crucial for implementing effective data privacy strategies.
1. Ransomware Attacks
Ransomware continues to be a dominant threat in healthcare. Attackers encrypt critical data and demand payment for its release, often disrupting hospital operations and compromising patient care.
2. Insider Threats
Employees or contractors with access to sensitive data can intentionally or unintentionally cause breaches. These threats are challenging to detect and can lead to significant data exposure.
- Types: Malicious insiders, negligent employees, and third-party vendors.
- Impact: Unauthorized access to patient records, leading to potential misuse or theft of information.
3. Phishing and Social Engineering
Cybercriminals use deceptive emails, messages, or websites to trick healthcare staff into revealing login credentials or downloading malicious software.
- Prevalence: Over 90% of healthcare cyberattacks are initiated through phishing attempts.
- Risk: Compromise of login credentials, leading to unauthorized access to sensitive data.
4. IoT and Medical Device Vulnerabilities
The proliferation of Internet of Things (IoT) devices in healthcare, such as MRI machines and infusion pumps, introduces new entry points for cyberattacks.
- Issue: Many devices have weak security measures, making them susceptible to exploitation.
- Consequence: Potential unauthorized access to patient data and disruption of medical services.
5. Cloud Security Risks
While cloud services offer scalability and flexibility, they also present challenges in data privacy and security.
- Concerns: Misconfigured cloud settings, inadequate access controls, and third-party vulnerabilities.
- Impact: Exposure of sensitive patient data and potential non-compliance with regulations.
6. Third-Party Vendor Risks
Healthcare organizations often rely on third-party vendors for various services, which can introduce additional security risks.
- Challenges: Ensuring vendors adhere to stringent data privacy standards and managing shared access to sensitive information.
- Risk: Breaches originating from third-party vendors can affect the healthcare organization's data integrity.
7. Regulatory Non-Compliance
Failure to comply with evolving data privacy regulations can lead to legal consequences and loss of patient trust.
- Regulations: HIPAA, GDPR, and other regional laws.
- Consequences: Fines, legal actions, and reputational damage.
8. Data Retention and Disposal Issues
Improper handling of data retention and disposal can lead to unauthorized access to outdated or unnecessary patient information.
- Problems: Failure to securely delete or anonymize data.
- Risks: Exposure of sensitive information and potential legal liabilities.
To address these evolving threats, healthcare organizations must adopt a proactive approach to cybersecurity. Implementing robust security measures, conducting regular training, and ensuring compliance with data privacy regulations are essential steps in safeguarding patient information. Organizations like WaferWire offer comprehensive solutions to help healthcare providers navigate these challenges and enhance their data privacy frameworks.
Modern Security Technologies Protecting Healthcare Data
As healthcare organizations digitize operations and embrace cloud computing, AI, and connected medical devices, safeguarding patient data requires more than conventional security measures. In 2025, a layered approach combining advanced technologies ensures data privacy, compliance, and operational efficiency. Here’s a detailed look at the top technologies transforming healthcare security:
1. Zero Trust Architecture (ZTA)
Zero Trust Architecture operates under the principle: never trust, always verify. Instead of assuming internal networks are safe, ZTA continuously authenticates every user, device, and application accessing healthcare data.
- Implementation: Identity verification, device health checks, least-privilege access, and micro-segmentation of networks.
- Benefits: Prevents lateral movement by attackers within hospital networks, minimizes insider threat exposure, and reduces risk across hybrid and cloud environments.
- Healthcare Impact: Protects sensitive EHRs and telehealth platforms from unauthorized access while supporting remote workforces and multi-location facilities.
2. Blockchain for Data Integrity
Blockchain provides immutable, auditable records for healthcare transactions, ensuring that data cannot be altered without detection.
- Use Cases: Secure sharing of patient records, tracking drug supply chains, and validating clinical trial data.
- Advantages: Enhances transparency, prevents tampering, and builds trust among providers, payers, and patients.
- Healthcare Example: Hospitals can share patient data securely with specialists while maintaining a verified audit trail, reducing manual compliance efforts.
3. Homomorphic Encryption
Homomorphic encryption allows computations on encrypted data without decryption, preserving confidentiality throughout analysis.
- Applications: Enables researchers to run analytics on sensitive patient datasets without ever exposing raw information.
- Benefits: Supports AI-driven diagnostics and predictive analytics while maintaining full compliance with HIPAA and other privacy regulations.
- Healthcare Impact: Hospitals and labs can collaborate on large-scale data analysis, improving outcomes without risking patient privacy.
4. AI-Powered Threat Detection
Machine learning algorithms continuously monitor networks and endpoints for unusual activity, identifying threats before they escalate.
- Capabilities: Detect ransomware patterns, phishing attempts, anomalous access behavior, and insider threats.
- Advantages: Real-time alerts and automated response reduce breach impact and operational downtime.
- Healthcare Impact: AI helps hospitals maintain continuous operations while securing patient data, especially during high-volume periods or crises.
5. Device-Bound Passkeys
Device-bound passkeys provide phishing-resistant authentication by linking credentials to specific hardware.
- Technology: Uses cryptographic keys stored on devices to replace passwords or SMS-based verification.
- Benefits: Reduces account takeover risks and simplifies secure access for healthcare staff.
- Healthcare Impact: Doctors and nurses can securely access patient systems on mobile devices without compromising security.
6. Secure Cloud Infrastructure
Cloud adoption is accelerating in healthcare, and secure cloud platforms provide built-in protections for sensitive data.
- Features: End-to-end encryption, automated compliance monitoring, multi-region backups, and granular access controls.
- Advantages: Scalability for growing data volumes, centralized management, and consistent compliance enforcement.
- Healthcare Impact: Providers can run analytics, AI models, and patient portals with confidence that data remains protected.
7. Secure Access Service Edge (SASE)
SASE converges network and security services into a single cloud-delivered model, providing secure connectivity for distributed healthcare systems.
- Components: Secure web gateways, cloud access security brokers (CASB), and zero-trust network access (ZTNA).
- Benefits: Simplifies security management for multi-site hospitals and remote clinics.
- Healthcare Impact: Enables secure telehealth sessions, remote monitoring, and multi-location collaboration without compromising data privacy.
8. Privacy-Enhancing Computation
Techniques like differential privacy, federated learning, and secure multi-party computation allow data analysis without exposing individual records.
- Applications: AI model training on decentralized datasets while preserving anonymity.
- Benefits: Enables predictive analytics, research collaboration, and patient outcome optimization without violating privacy regulations.
- Healthcare Impact: Hospitals can leverage insights across systems and partners while maintaining strict privacy safeguards.
These technologies are most effective when integrated into a holistic security strategy. Simply deploying tools is not enough, operational processes, staff training, and regulatory alignment must accompany technological adoption.
Best Practices for Data Privacy in Healthcare Organizations

Ensuring healthcare data privacy is no longer optional, it’s central to operational integrity, regulatory compliance, and patient trust. As organizations handle increasing volumes of sensitive patient information across cloud, edge, and IoT devices, adopting a robust framework of best practices becomes essential.
1. Implement Robust Access Controls and Identity Management
Role-based access control (RBAC) and identity verification are foundational to data privacy:
- Role-Based Access Control (RBAC): Assign permissions based on roles rather than individuals. For instance, nurses may access patient vitals but not financial records, while administrators can review billing data.
- Multi-Factor Authentication (MFA): Combine passwords with security tokens or biometric verification to prevent unauthorized access.
- Adaptive Access Policies: Contextual checks based on device, location, and time of access further reduce risk.
- Example in Action: A hospital implementing MFA and RBAC saw a 70% reduction in credential-based breaches across its cloud applications.
2. Continuous Data Monitoring and Audit Trails
Ongoing monitoring helps detect anomalies and enforce accountability:
- Activity Logging: Track every access, modification, or transfer of sensitive patient data.
- Anomaly Detection: AI-driven monitoring identifies unusual access patterns, e.g., a user downloading large volumes of records outside working hours.
- Regulatory Compliance: Detailed audit trails support HIPAA and GDPR reporting requirements.
- Best Practice: Integrate monitoring tools that automatically alert security teams to suspicious behavior in real-time.
3. Data Encryption at Rest and in Transit
Encryption ensures that data remains unreadable to unauthorized parties:
- At Rest: Encrypt databases, storage accounts, and backups. AES-256 is the current industry standard.
- In Transit: Protect data moving between devices, cloud platforms, and applications using TLS 1.3.
- Healthcare Impact: Protects electronic health records (EHRs) and telehealth sessions, even if network or storage vulnerabilities exist.
- Real-World Example: A clinic adopting end-to-end encryption on its telemedicine platform reduced potential HIPAA violations from intercepted communications.
4. Staff Training and Security Awareness Programs
Human error remains a leading cause of healthcare data breaches:
- Regular Training: Employees learn phishing detection, secure password management, and proper handling of patient data.
- Simulated Phishing Tests: Reinforces learning and identifies staff needing additional training.
- Culture of Security: Employees become active participants in data protection, not just passive users.
5. Zero Trust Security Model
Zero Trust assumes that no actor, device, or network segment is automatically trusted:
- Principles: Always authenticate, authorize, and continuously validate access for every request.
- Micro-Segmentation: Limits lateral movement for attackers within hospital networks.
- Adaptive Enforcement: Access rules dynamically adjust based on user behavior and device health.
6. Automated Backups and Disaster Recovery Plans
- Cloud Backup Solutions: Store encrypted copies of patient records in geographically distributed data centers.
- Recovery Objectives: Define Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) to minimize downtime.
- Testing and Drills: Periodically test disaster recovery plans to ensure rapid data restoration.
- Healthcare Example: A hospital group used cloud replication to recover critical patient data within minutes after a ransomware attack, avoiding operational shutdown.
7. Vendor Risk Management
- Third-Party Assessments: Evaluate cloud providers, SaaS applications, and medical device vendors for security compliance.
- Contracts and SLAs: Ensure agreements include encryption, breach notification, and audit rights.
- Continuous Monitoring: Track vendor security practices over time, not just at onboarding.
Adopting these practices alone is not enough, modern healthcare organizations require integrated solutions that tie these practices to data modernization and AI readiness. WaferWire helps providers implement these strategies within a unified, secure, and compliant data estate, leveraging Microsoft Fabric and cloud infrastructure to operationalize security and privacy seamlessly.
Future Trends in Healthcare Data Privacy & Security
The landscape of healthcare data privacy and security is rapidly evolving. Emerging technologies, changing regulations, and patient expectations are driving a transformation that healthcare organizations must anticipate to remain compliant, efficient, and competitive.
1. AI-Powered Security and Threat Detection
- Predictive Threat Intelligence: Machine learning models analyze network traffic and access patterns to predict breaches before they occur.
- Automated Incident Response: AI can isolate compromised accounts, trigger alerts, and remediate threats autonomously.
- Impact: Hospitals and clinics reduce downtime, prevent data leaks, and optimize security team efficiency.
2. Privacy-Enhancing Computation Techniques
- Federated Learning: Train AI models across multiple hospitals without centralizing patient data.
- Differential Privacy: Add noise to datasets to protect individual records while preserving analytic value.
- Secure Multi-Party Computation: Enables collaborative analytics without exposing sensitive data.
- Healthcare Use Case: Multiple research hospitals can analyze disease trends collectively without violating patient privacy.
3. Integration of Cloud and Edge Security
- Edge Computing Security: Medical devices and IoT sensors process data locally while maintaining privacy.
- Cloud Integration: Data syncs securely to central cloud platforms for analytics and storage.
- Benefits: Real-time patient monitoring, faster insights, and reduced exposure of sensitive data to transmission risks.
4. Regulatory Evolution and Global Compliance
- Cross-Border Regulations: Increasing demand for international compliance frameworks beyond HIPAA and GDPR.
- Adaptive Solutions: Organizations must adopt flexible systems that accommodate different data privacy laws.
- WaferWire’s Role: Assists with compliance automation and continuous monitoring to adapt to evolving regulations.
5. Zero Trust Becomes Standard
- Widespread Adoption: From large hospital networks to small clinics, Zero Trust will become a baseline requirement.
- Continuous Verification: Every access attempt, device, and application undergo verification in real time.
- Outcome: Reduced risk of insider threats and lateral attacks across complex healthcare ecosystems.
6. Patient-Centric Privacy and Transparency
- Consent Management: Patients will have greater control over who accesses their data and for what purpose.
- Data Portability: Seamless transfer of records between providers without compromising security.
- Trust & Engagement: Enhances patient confidence in digital health services.
7. AI-Driven Compliance and Automation
- Automated Compliance Checks: AI evaluates policies, identifies gaps, and recommends corrections.
- Policy Enforcement: Automatically applies security rules and tracks violations.
- Healthcare Impact: Reduces administrative burden and ensures regulatory alignment continuously.
8. Cyber-Resilience and Incident Preparedness
- Proactive Simulations: Regular drills and AI-driven attack simulations prepare teams for real-world scenarios.
- Redundancy Planning: Multi-cloud and hybrid strategies ensure uninterrupted operations during breaches or outages.
- Future Outlook: Cyber-resilient hospitals maintain patient care without disruption while rapidly mitigating threats.
WaferWire: Seamlessly Integrating Data Estate Modernization in Healthcare
Healthcare organizations face complex data landscapes with patient information flowing from EHRs, IoT devices, and cloud platforms. Legacy systems struggle to keep up, limiting AI-readiness, increasing costs, and creating operational bottlenecks. WaferWire addresses these challenges by building unified, intelligent data estates powered by Microsoft Fabric, transforming data into actionable insights efficiently and securely.
Key Solutions by WaferWire
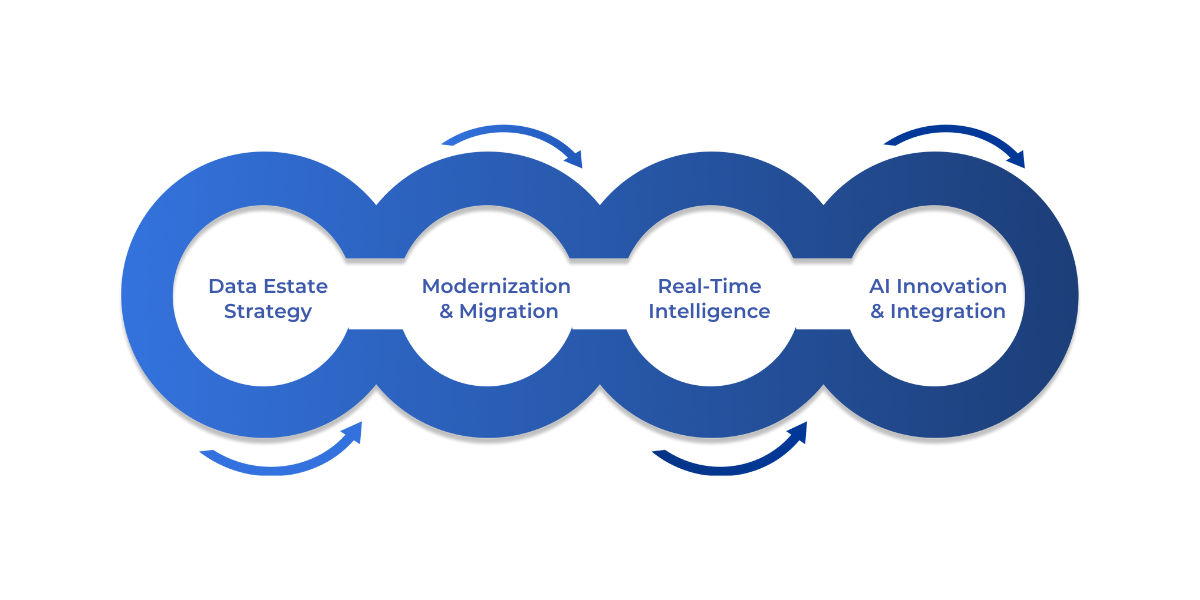
- Data Estate Strategy & Consulting: Align data with business goals, reduce reporting cycles from 3 days to 2 hours, and optimize infrastructure costs by up to 40%.
- Modernization & Migration: Accelerate migration to Microsoft Fabric with minimal disruption, preserving existing reports and models while deploying workloads in weeks.
- Real-Time Intelligence: Enable live analytics across operations, track patient vitals, monitor workflows, and automate alerts for faster responses.
- AI Innovation & Integration: Embed AI into workflows for automated insights, faster decision-making, and natural language querying of large datasets.
Why WaferWire Stands Out
- Expertise with 20+ global clients and five locations.
- Azure Innovate partner, implementing Microsoft Fabric for enterprise-ready healthcare solutions.
- Ready-to-deploy accelerators shorten time-to-value while ensuring long-term scalability and compliance.
Modern healthcare demands an integrated, intelligent data foundation that supports AI, analytics, and operational efficiency. WaferWire’s Data Estate Modernization ensures organizations meet 2025’s data challenges while preparing for future innovation.
Conclusion
Protecting healthcare data privacy in 2025 isn’t just a regulatory checkbox, it’s a commitment to patient trust, operational resilience, and the longevity of your organization. As cyber threats grow more sophisticated, adopting advanced security measures, leveraging cloud solutions, and embedding privacy-by-design principles are no longer optional.
WaferWire is committed to helping healthcare organizations navigate this evolving landscape with tailored solutions in data protection, compliance readiness, and secure cloud adoption. From strategic assessments to hands-on implementation, we bridge the gap between security goals and real-world execution.
Ready to safeguard your healthcare data?
[Book a free consultation] Our experts at WaferWire can assess your current privacy framework and help you strengthen compliance, security, and patient trust.
FAQs
1. What is the biggest data privacy challenge for healthcare in 2025?
Ransomware and phishing remain top threats, but the rise of AI-driven cyberattacks is making real-time detection essential.
2. How can cloud adoption improve healthcare data security?
Cloud platforms offer built-in encryption, continuous monitoring, and disaster recovery, if configured with strict compliance and access controls.
3. Is compliance enough to protect healthcare data?
No. Compliance ensures baseline requirements, but true security demands continuous risk assessment and proactive threat mitigation.
4. How can WaferWire help healthcare organizations?
WaferWire provides strategic consulting, compliance audits, cloud migration services, and end-to-end security implementation tailored for healthcare.
5. What’s the best starting point for improving data privacy?
Begin with a comprehensive privacy and security audit to identify vulnerabilities, followed by a prioritized action plan.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)