
Understanding Incident Response and Management with Automation
Murthy S
2025-03-17

Talk to our cloud experts
Subject tags
As cyber threats evolve at an unprecedented pace, businesses can no longer rely on slow, manual incident response methods. By integrating automation into incident management, organizations can reduce response times and alert fatigue and strengthen their security posture without overburdening their teams.
One of the most effective solutions leading this shift is PagerDuty Incident Response, a dynamic platform that enables real-time alerting, automated workflows, and seamless collaboration. This platform ensures a faster, more efficient response to security incidents, enabling teams to focus on what matters most.
This article explores how automated incident response improves efficiency, enhances decision-making, and ensures rapid threat containment. By doing so, it helps organizations reduce risk, save time, and strengthen their overall security posture. Let’s dive in.
Importance of Incident Response and Management
Cybersecurity incidents are no longer a question of "if" but "when." The real challenge isn’t just detecting threats—it’s how fast and effectively organizations can respond. A slow response can lead to data breaches, financial losses, and reputational damage, while an efficient, well-managed incident response strategy minimizes impact and ensures business continuity.
Rapid Breach Containment and Threat Mitigation
Every second counts when responding to an incident. Cybercriminals move fast, exploiting vulnerabilities and escalating attacks within minutes. A disorganized response leads to delayed containment, prolonged downtime, and severe data loss.
An effective incident response strategy includes the following key elements:
- Early threat detection through continuous monitoring and intelligent alerting.
- Execution of pre-defined response actions to isolate affected systems.
- Adherence to structured playbooks by security teams, reducing confusion and errors.
Safeguarding Business Reputation and Revenue
Effective incident management is crucial for mitigating risks such as data breaches, financial losses, and reputational damage. By implementing a structured incident response plan, organizations can minimize the impact of breaches and protect their business on multiple fronts. Here’s how:
- Protects customer data: A swift response ensures that customer information is secure, helping the organization stay compliant with regulations such as GDPR, CCPA, and PCI-DSS. This not only prevents legal issues but also maintains customer confidence.
- Prevents financial losses: According to the IBM Report, the average data breach cost in 2023 was $4.45 million, marking a 15% increase over the past three years. However, organizations with a well-defined incident response plan can significantly reduce the likelihood of breaches and mitigate their financial impact.
- Preserves brand credibility: In the wake of a security breach, how quickly and effectively an organization responds can influence its public reputation. A fast and well-executed response minimizes the damage to the brand, helping maintain trust with customers and stakeholders.
Centralized Incident Management for Seamless Coordination
Disjointed security operations lead to miscommunication, inefficient response efforts, and unresolved threats. Without a centralized system, security teams often waste time sifting through logs, juggling tools, and manually escalating incidents.
Implementing a centralized incident management system offers several advantages:
- Improved Communication and Collaboration: Centralizing incident information enhances communication among team members, leading to quicker decision-making and more effective responses.
- Enhanced Efficiency: Automated task assignments and standardized workflows streamline operations, reducing the time spent on manual processes and minimizing errors.
- Cost Savings: A structured incident management framework can significantly reduce costs by enabling faster incident resolution and minimizing downtime.
Incident response alone is not enough—automation is the next frontier. The next section explores how AI-driven automation enhances incident triage, reduces manual workload, and accelerates security operations.
Automation in Incident Response
A security incident can escalate from a minor anomaly to a full-blown breach within minutes. With advanced automation tools like PagerDuty Incident Response, organizations can detect, contain, and remediate threats with unparalleled speed—all while reducing the burden on security teams.
Transforming Security Operations with Automation
Manual incident response is inefficient and prone to human error. Security teams often juggle multiple tools, logs, and alerts, leading to slow decision-making and miscommunications. Automated incident response eliminates these mistakes by instantly detecting threats, executing predefined actions, and ensuring seamless team coordination. Instead of manually analyzing incidents, automation filters out false positives, correlates security events, and applies AI-driven risk assessments, allowing security analysts to focus on genuine threats.
PagerDuty’s Role in Orchestrating a Unified Response
Incident response often involves multiple tools, platforms, and teams. PagerDuty Incident Response helps coordinate this complex process by bringing all security alerts into a single, actionable dashboard. With automated escalation and task assignments, PagerDuty ensures that the right teams are engaged immediately, facilitating seamless collaboration across security, DevOps, and IT teams for faster, more efficient responses.
Automation makes incident response faster and more reliable, but a structured approach is critical to ensuring consistency. Next, we break down the key steps in the incident response process, ensuring that every security event is handled precisely and efficiently.
Steps in the Incident Response Process
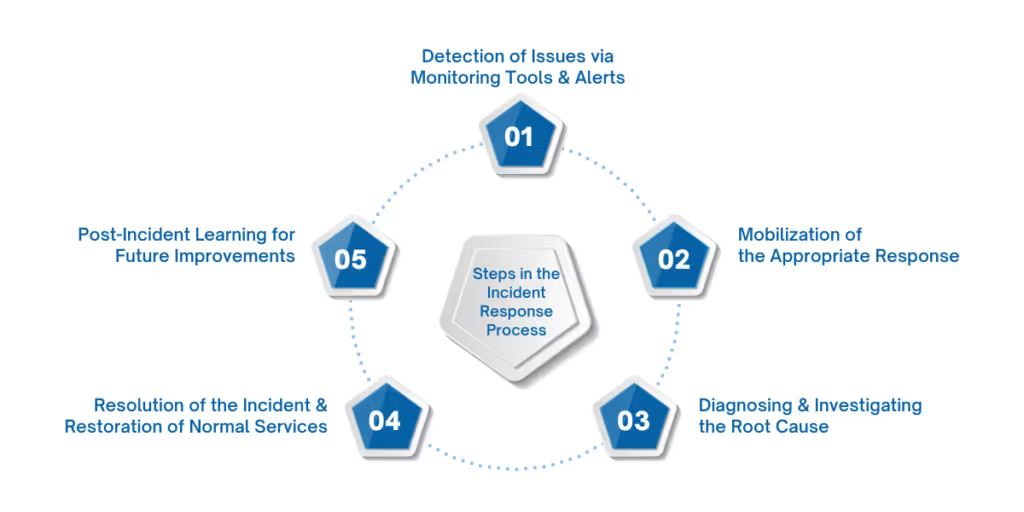
Handling a security incident is no easy task. It requires a structured, methodical approach to minimize damage and restore services quickly. Each step plays a critical role in managing and resolving the issue effectively.
1. Detection of Issues via Monitoring Tools and Alerts
The first sign of a potential issue often comes through monitoring tools and alerts. These tools constantly scan your systems for abnormal behavior. Whether it’s a network intrusion or suspicious user activity, detecting these early can prevent bigger problems later.
2. Mobilization of the Appropriate Response
Once an incident is detected, the right team must act fast. The team’s role depends on the severity of the threat. PagerDuty Incident Response can help assign the appropriate team members based on the incident’s nature, ensuring that skilled personnel are mobilized without delay.
3. Diagnosing and Investigating the Root Cause
After the response team is in place, they start diagnosing the problem. Was it a cyberattack or a system failure? Identifying the root cause is critical for preventing similar issues in the future. Using automated workflows, security teams can quickly gather relevant data, saving valuable time during this phase.
4. Resolution of the Incident and Restoration of Normal Services
Once the cause is understood, resolving the issue becomes the top priority. With automated tools, teams can quickly isolate affected systems and restore services. PagerDuty’s streamlined workflows ensure every team member can collaborate in real time, reducing overall downtime.
5. Post-Incident Learning for Future Improvements
After the incident is resolved, it’s time for reflection. What went well? What could have been done differently? This step allows organizations to learn and improve their processes for future incidents. Integrating lessons learned from each incident into the response strategy ensures that teams are always prepared.
Now that we have outlined the steps, let’s explore the key roles that ensure a smooth incident response.
Key Roles in Incident Response and Management
When a security incident hits, having a well-organized team is crucial. The roles within the team ensure that everything is handled smoothly and efficiently, minimizing disruption. Each role is designed to manage a specific response aspect, making the entire process more effective.
- Incident Commander: The incident commander leads the entire response effort. They make critical decisions and ensure everything runs according to plan. This role requires clear thinking and quick action to direct the response team and minimize chaos during high-pressure situations.
- Deputy: The deputy supports the incident commander and is responsible for assisting with decisions and ensuring all areas of the incident are covered. They provide backup leadership and ensure that tasks are assigned correctly, keeping the process organized.
- Scribe: Documentation is key to understanding and improving future responses. The Scribe records every action taken during the incident. This helps ensure transparency and creates a detailed account of what happened, which is useful for later analysis.
- Internal and Customer Liaisons: These individuals handle communication with both internal teams and customers. They ensure that everyone is informed about the situation and the actions being taken. They act as the company's voice, maintaining trust and clarity in a crisis.
- Subject Matter Experts: These experts focus on the technical side of incident resolution. Whether identifying the cause of the breach or implementing a fix, they bring specialized knowledge to handle the most complex aspects of an incident.
Once the roles are clearly defined, the next step is to integrate the right tools for managing the incident effectively.
Integrating Incident Management Tools
Efficient incident management doesn’t just rely on people—it also needs the right tools. Integrating the right systems ensures the response is fast, organized, and effective. Below are some key integrations that streamline incident handling.
- Integrating PagerDuty Incident Response: PagerDuty Incident Response is crucial for coordinating team responses. Integrating this tool lets you consolidate alerts and assign tasks in real time, ensuring faster response times and clearer communication across departments.
- API Key Management and Secure Storage: Security is key when dealing with incident management. Tools like AWS Secrets Manager help store sensitive API keys securely. This ensures that your team can access necessary information without compromising security.
- Create Detailed Response Plans: Having predefined response plans is essential for a quick and organized response. Integrating these plans with monitoring tools helps to automatically trigger the necessary workflows when an incident is detected, reducing delays in the response process.
After integrating the tools, the next critical phase is learning from the incident to improve future responses.
Post-Incident Analysis and Learning
Once the immediate threat is contained and resolved, the next step is reflection. Incident management doesn’t stop when the crisis ends. A post-incident review is essential to improving future responses. It helps identify weaknesses and fine-tune processes.
Conduct Analysis for Continuous Improvement
Each incident offers a valuable learning opportunity. It is crucial to analyze what went right and what went wrong. This analysis highlights areas where processes can be streamlined and improvements made. With every response, teams grow stronger and faster.
Update Processes and Address Legacy Issues
Older systems or outdated procedures can be obstacles during an incident. Addressing legacy issues ensures smoother responses in the future. It’s about making changes that have long-lasting effects. The goal is to adapt quickly and eliminate recurring inefficiencies.
Develop Action Items from Post-Mortem Findings
The post-mortem is more than just a report. It’s a set of action items based on lessons learned, which form the roadmap for improvement. With clear action points, teams can stay prepared for the next challenge. This proactive approach to learning strengthens security defenses.
It's time to explore the clear benefits of automating incident management.
Benefits of Automated Incident Management
Automating incident management does more than speed up the process. It enhances the quality of the response, reduces human error, and provides consistency across teams.
Reduces Response Time and Human Error
Time is critical during an incident. The quicker the response, the less damage is done. Automation helps reduce response times by instantly triggering predefined actions. It also minimizes the potential for human error, ensuring that every step is executed as planned.
Ensures Consistent and Reliable Incident Handling
Automation ensures that every incident is handled the same way. By setting standardized workflows, all teams follow the same process. This creates consistency, no matter how big or small the incident. Every response is dependable, increasing the reliability of your security operations.
Enhances Customer Experience by Rapid Resolutions
When a security incident occurs, customers expect quick resolutions. Automated workflows ensure that the teams are informed and equipped to resolve issues swiftly. Fast responses translate to less downtime and a better customer experience. By improving incident resolution time, companies build stronger relationships with their customers.
Conclusion
Speed and precision are non-negotiable in security. Integrating automation, like PagerDuty Incident Response, empowers your team to act faster and more accurately, reducing downtime and preventing costly errors. But it’s not just about reacting; it’s about constantly improving. Every incident teaches valuable lessons, strengthening your defenses.
WaferWire brings this proactive approach to life. We help businesses integrate cutting-edge tools and continuously optimize processes to stay one step ahead. The question isn't if you’ll face a security challenge—it’s when. When it happens, be ready with PagerDuty incident response and WaferWire’s expertise to ensure your business can recover swiftly and emerge stronger.
Get in touch with us today and start transforming your security strategy.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)












