Ransomware Trends 2025: How US Businesses Can Stay Secure from Attacks
Mownika
7th Sept 2025

Talk to our cloud experts
Subject tags
Ransomware groups are shifting their tactics from encryption to data exfiltration, using advanced programming languages like Rust and Go for more sophisticated attacks. Exploiting software vulnerabilities and merging with hacktivist movements, they complicate the threat landscape.
This blog explores emerging trends, evolving tactics, and strategies U.S. businesses can adopt to stay secure.
Key Takeaways:
- Ransomware attacks are increasingly sophisticated, shifting from encryption to data exfiltration using advanced languages like Rust and Go.
- U.S. businesses, especially SMBs, are being heavily targeted, with average losses reaching $1.85 million.
- Ransomware groups are forming alliances and adapting new tactics like AI-driven social engineering and RaaS, making detection and defense more challenging.
- Implementing a multi-layered defense strategy, training employees, and developing incident response plans are crucial for staying secure.
- The rise of AI and evolving attack methods require businesses to be agile and proactive in their cybersecurity efforts.
Ransomware Group Dynamics in 2025
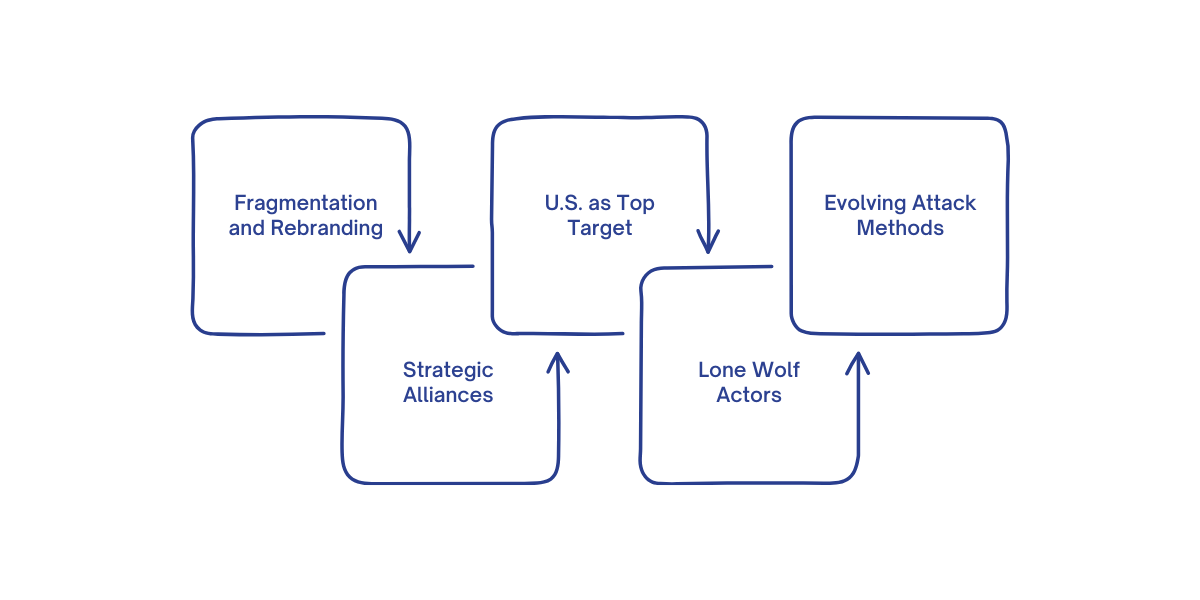
The ransomware industry in 2025 is marked by constant fragmentation and rebranding. New groups emerge frequently, while older ones disappear or merge, often forming strategic alliances.
The U.S. remains the top target, and industries like technology, manufacturing, and healthcare are frequently attacked. The rise of independent "lone wolf" actors adds unpredictability, especially for SMBs.
Now, let’s explore the innovative tactics being employed by ransomware groups today.
Evolving Ransomware Tactics
Ransomware groups have refined their methods, incorporating RaaS, triple extortion, and AI-driven social engineering to increase the effectiveness of their attacks. These tactics make detection harder and amplify pressure on victims.
- Ransomware-as-a-Service (RaaS): Lowers the entry barrier for cybercriminals, leading to a surge in attacks and greater fragmentation.
- Double and Triple Extortion: Attackers encrypt data, threaten public release, and may add DDoS attacks or regulatory reporting to increase pressure on victims.
- AI-Enhanced Social Engineering: Phishing and social engineering attacks, powered by AI, bypass technical defenses and exploit human vulnerabilities.
- AI-Driven Evasion: Improved malware evasion techniques and reconnaissance make it harder to detect ransomware before impact.
- Advanced Evasion Tools: Attackers use tools like Crypto24's RealBlindingEDR and RansomHub's EDRKillShifter to bypass endpoint protections.
To stay ahead of these increasingly sophisticated threats, businesses must adopt proactive strategies. Here are key actions you can take to safeguard your organization.
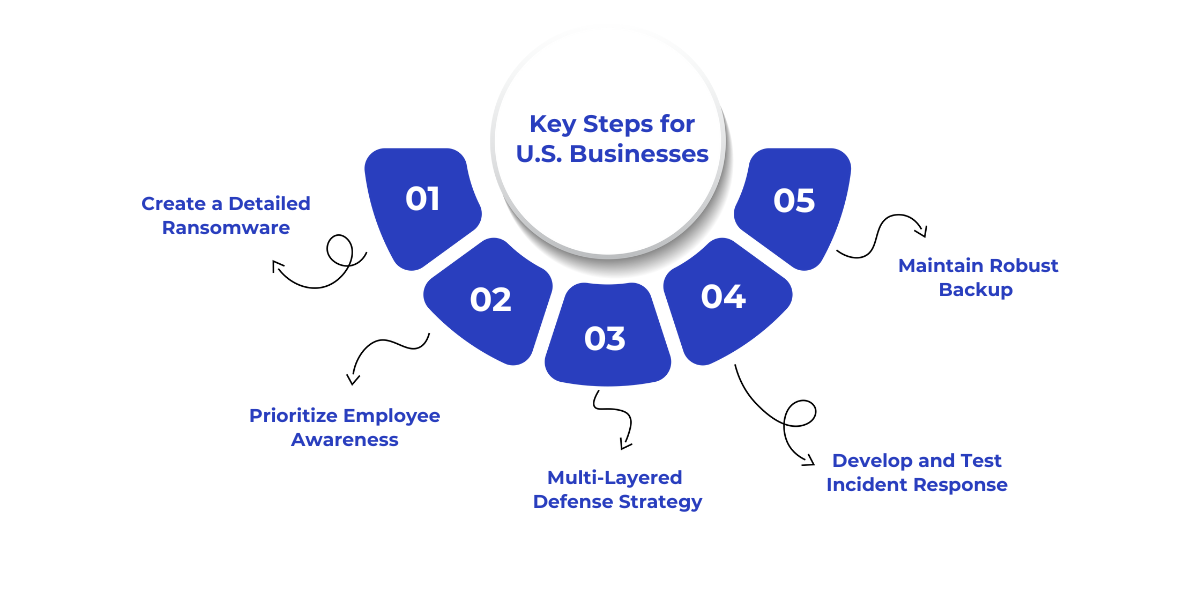
Key Steps for U.S. Businesses to Combat Ransomware Attacks in 2025
This low risk allows attackers to operate with increasing confidence, heightening the need for businesses to take stronger preventative measures.
Some key strategies that businesses can implement include:
Step 1: Create a Detailed Ransomware Response Playbook
Develop a ransomware playbook with clear action steps for various attack scenarios. This should define roles, responsibilities, and communication protocols, enabling a fast and coordinated response to mitigate damage during an attack.
Step 2: Prioritize Employee Awareness and Training
Since human error is a key factor in many ransomware breaches, invest in regular training programs to help employees recognize phishing attempts and other social engineering tactics.
Use scenario-based exercises and phishing simulations to build a well-informed workforce.
Step 3: Implement a Multi-Layered Defense Strategy
Strengthen your security by deploying a multi-layered approach that includes Endpoint Detection and Response (EDR) systems, network-based detection, multi-factor authentication (MFA), and a Zero Trust model. These layers of protection minimize the risk of ransomware infiltrating your systems.
Step 4: Develop and Test Incident Response and Recovery Plans
Establish comprehensive incident response and recovery plans and regularly conduct security exercises, tabletop simulations, and breach response drills. These activities ensure your team is prepared to handle real-world ransomware attacks and enhances overall recovery efficiency.
Step 5: Maintain Robust Backup and Patch Management Practices
Ensure your data is regularly backed up and recovery systems are tested. Implement automated patch management to reduce vulnerabilities, allowing for quick recovery from ransomware attacks and reducing the risk of exploitation through outdated software.
Also Read: Healthcare Data Privacy and Security Evolution in 2025
With ransomware becoming more complex, the right investment in cybersecurity is crucial. Let’s discuss how businesses can allocate resources wisely to combat these threats effectively.
Strategic Budgeting and Security Advancements Against Threats
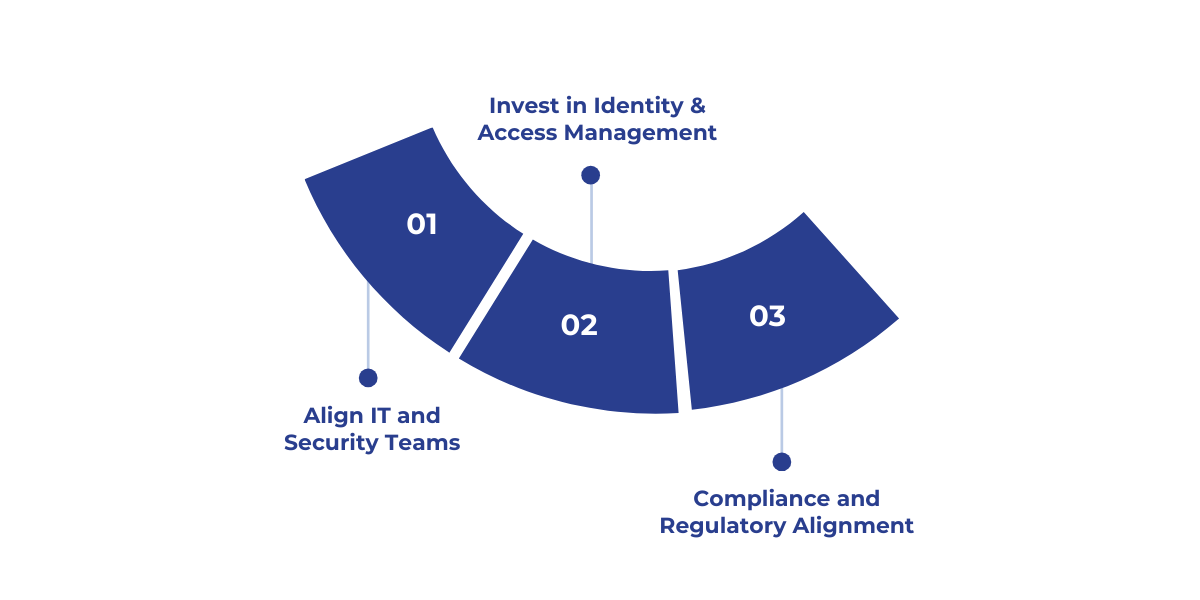
As ransomware threats grow, U.S. businesses are boosting cybersecurity budgets with a risk-based approach, prioritizing resources based on potential impact.
As ransomware becomes more sophisticated, investing in advanced detection and recovery tools is crucial.
Key Focus Areas:
- Align IT and security teams: Collaboration between IT, security, and operational teams helps ensure that cybersecurity is a business-enabler, not just a technical function. Cross-functional security units can manage shared threat intelligence and incident response effectively.
- Invest in identity and access management (IAM): A Zero Trust model with role-based access controls and continuous monitoring can prevent unauthorized access and reduce the attack surface.
- Compliance and regulatory alignment: Ensuring security investments align with regulatory frameworks like HIPAA, NIST, and CMMC will streamline efforts and improve compliance.
While prevention is critical, having a recovery plan in place is just as important. Here’s how you can minimize the impact and recover quickly if an attack occurs.
Post-Attack Recovery Practices
Even with robust defenses, no business is immune to ransomware attacks. A comprehensive post-attack recovery plan is essential to minimize operational disruption and financial losses. Key aspects of this plan include:
- Fast isolation of affected systems: Rapid isolation of infected systems limits the spread of the ransomware and helps protect other critical assets.
- Engage cyber insurance: Having cyber insurance can help mitigate the financial burden of a ransomware attack, covering costs such as ransom payments, recovery efforts, and legal fees.
- Review and strengthen defenses: After an attack, businesses should conduct a thorough review to identify weaknesses in their defenses and address them to prevent future incidents.
Impact of Ransomware on Critical Infrastructure
Ransomware is increasingly targeting critical infrastructure, with severe consequences for national security and public safety:
Ransomware's Impact on SMBs: Why They’re Prime Targets
Small and medium-sized businesses (SMBs) are increasingly targeted by ransomware due to weaker defenses, financial pressure, and reliance on third-party vendors. These factors make SMBs vulnerable to attacks and often drive them to pay ransoms to recover
Also Read: Introduction to Microsoft Fabric for Small and Medium-Sized Enterprises
Preparing for the Future: Adapting to Emerging Threats
Artificial Intelligence (AI) is changing ransomware tactics, enabling cybercriminals to automate and accelerate their attacks. Key areas where AI enhances ransomware operations include:
- Target Identification: AI can scan systems for vulnerabilities far more efficiently than manual methods, helping attackers pinpoint profitable targets.
- Social Engineering: AI powers hyper-realistic phishing schemes that exploit human emotions, significantly increasing the success rate of attacks.
- Malware Evasion: AI-driven malware adapts in real time, evading traditional security measures and bypassing signature-based detection systems.
Conclusion
As ransomware groups continue to evolve in 2025, U.S. businesses must stay ahead of emerging threats through proactive security measures. By integrating advanced detection tools, refining response strategies, and ensuring robust cybersecurity protocols, organizations can mitigate risks and reduce the impact of attacks.
Secure your business with WaferWire's tailored cloud services, AI-driven strategies, and advanced analytics. Contact us today to enhance your cybersecurity and ensure compliance without slowing down your growth.
FAQs
Q: What makes the healthcare industry a primary target for ransomware?
A: Healthcare organizations are prime targets due to the high value of sensitive medical data, the urgency of services they provide, and often outdated or inadequate cybersecurity measures. This makes them more likely to pay ransoms to restore services quickly.
Q: How do ransomware-as-a-service (RaaS) platforms contribute to the rise of attacks?
A: RaaS platforms lower the entry barriers for cybercriminals by offering ready-to-use ransomware tools, making it easier for less experienced attackers to launch sophisticated attacks. This has led to a significant increase in attack frequency and diversity.
Q: How does a ransomware attack impact an organization's reputation?
A: A ransomware attack can severely damage an organization's reputation by eroding customer trust, especially if sensitive data is exposed or services are disrupted. Rebuilding trust can take years and can lead to lost business opportunities.
Q: Why are small businesses more vulnerable to ransomware attacks?
A: Small businesses often lack the resources to implement robust security measures, making them easier targets for attackers. Additionally, many SMBs rely heavily on third-party vendors, which can create additional entry points for ransomware.
Q: What role does incident response play in minimizing the impact of ransomware?
A: A well-prepared incident response plan is crucial in minimizing ransomware damage. It ensures quick identification of the attack, containment of the breach, and timely communication with stakeholders, which can reduce downtime and financial losses.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)