
Understanding Role-Based Access Control in Microsoft Fabric
Mownika
30th Sept 2025

Talk to our cloud experts
Subject tags
As enterprises handle increasingly complex data and collaboration demands, securing access while maintaining operational efficiency is critical.
Role-based access control in Microsoft Fabric provides a structured way to manage permissions by assigning access based on roles instead of individuals, reducing risks and ensuring compliance.
Implementing role-based access control Fabric effectively requires understanding organizational roles, access hierarchies, and the interaction between workspaces, items, and service principals.
This guide offers a detailed overview of emerging trends in role-based access control Fabric, helping organizations strengthen security while enabling efficient collaboration and governance.
Key Takeaways
- Role-Based Access Control Fabric ensures secure, role-aligned access across workspaces, items, and compute.
- Defining roles such as Admin, Member, Contributor, and Viewer minimizes risks and streamlines collaboration.
- Extending Role-Based Access Control Fabric to service principals ensures secure automation and Azure integration.
- Best practices like least privilege, automation, and regular audits are critical for success.
- Emerging trends like AI-driven access and Zero Trust models will reshape RBAC strategies in the coming years.
Before diving into implementation, it’s important to understand the core features and advantages.
Role-Based Access Control Fabric: Key Features & Benefits
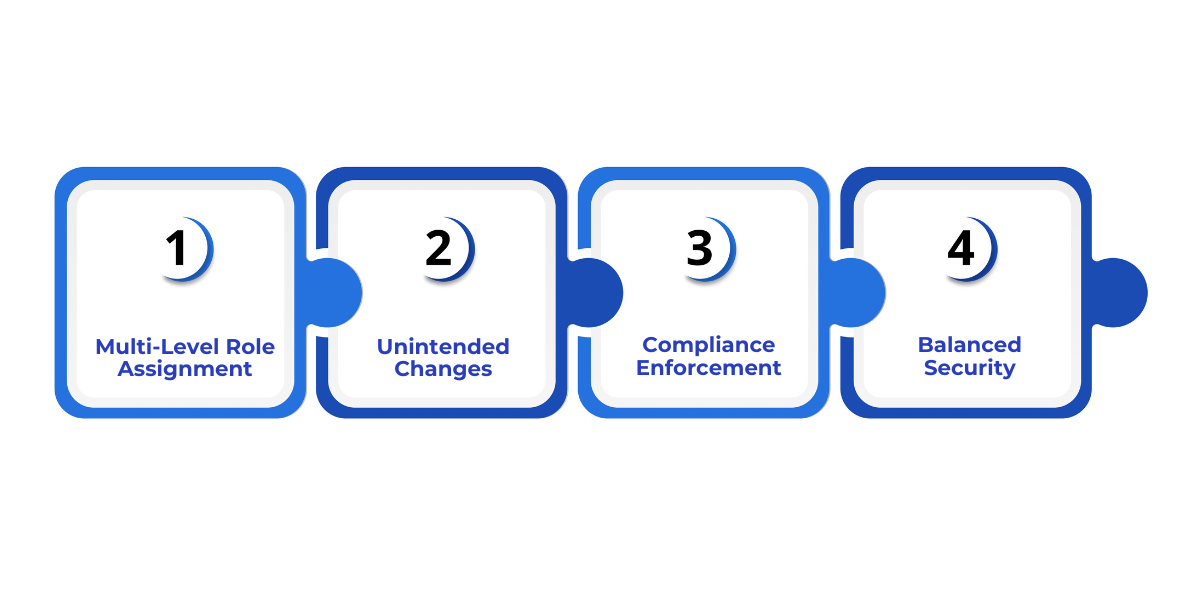
To start, RBAC in Microsoft Fabric offers a structured security model that assigns permissions based on roles rather than individual users. This approach helps organizations maintain compliance, safeguard sensitive data, and support team collaboration effectively.
Below are the key features and benefits of role-based access control in Microsoft Fabric:
- Multi-Level Role Assignment: Assign roles at workspace, item, and compute levels, ensuring access is granted only where needed and minimizing accidental changes.
- Prevention of Unintended Changes: Limit write permissions to safeguard datasets, reports, and pipelines, avoiding errors that disrupt analytics.
- Compliance Enforcement: Enforce consistent access rules across teams to meet GDPR, HIPAA, and SOC 2 standards.
- Balanced Security and Flexibility: Maintain control while enabling teams to work efficiently without exposing sensitive resources.
Clear Role Definitions:
- Microsoft Fabric provides predefined roles like Admin, Member, Contributor, and Viewer, so responsibilities align with permissions.
- Admins manage users and roles, Members can read/write data, Contributors create and modify content, and Viewers have read-only access.
Example: Consider a financial services firm where analysts and managers access critical reporting dashboards. RBAC ensures analysts can update datasets while executives can view KPIs without accidentally altering underlying data, maintaining operational efficiency and compliance.
Understanding these foundational features sets the stage for how RBAC controls access across different layers of Fabric, which we explore next.
How Does RBAC Enhance Security in Microsoft Fabric?

Protecting sensitive data while enabling team collaboration is critical for modern enterprises. Microsoft Fabric's architecture incorporates Role-Based Access Control (RBAC) to assign permissions by roles, ensuring security without slowing down workflows.
RBAC spans workspaces, individual assets, service principals, and compute resources, giving your organization precise control and compliance-ready governance.
Here’s how it works across your Fabric environment:
1. Defining Roles and Permissions at the Workspace Level
At the workspace level, RBAC defines user roles and responsibilities within collaboration hubs. This ensures teams have appropriate access while protecting critical business information:
- Admins: Oversee workspace membership, allocate resources, and configure access policies.
- Contributors: Publish, modify, and manage content within the workspace.
- Viewers: Access dashboards, reports, and insights with view-only permissions, preventing accidental changes.
This workspace-level control ensures data integrity while supporting collaborative workflows. Once workspace access is clear, it’s equally important to protect individual assets, which leads us to item-level permissions.
Also Read: Data Integration from Multiple Sources: Steps and Tips
2. Protecting Individual Assets with Item-Level Permissions
RBAC provides fine-grained control for individual assets, allowing organizations to protect sensitive data while enabling collaboration:
- Power BI Reports: Restrict editing rights while enabling read-only access for analysts.
- Semantic Models: Assign roles for model modifications and prevent unauthorized updates.
- Pipelines and Notebooks: Control access for editing, executing, or viewing data pipelines.
By applying RBAC at the item level, enterprises can enforce governance policies and safeguard sensitive insights, ensuring that only authorized personnel make changes.
With individual assets protected, the next critical step is securing automation and integrations using service principals.
3. Securing Automation Through Service Principal Permissions
Service principals, which enable automation and Azure integrations, are fully supported by RBAC, allowing enterprises to secure automated workloads:
- Secure Automation: Grant applications access only to the resources they need.
- Role-Based Workflows: Ensure automated processes follow assigned permissions.
- Prevent Unauthorized Background Processes: Stop non-compliant or unapproved tasks from executing.
This layer of RBAC is especially vital for regulated industries, such as healthcare and finance, where operational data security and compliance are non-negotiable.
After securing automated processes, RBAC also protects compute resources, enabling safe and efficient analytics workflows.
4. Managing Access to Compute Resources
Fabric’s SQL compute engine supports advanced analytics while protecting sensitive data:
- Schema and Table-Level Access: Grant access only to relevant datasets.
- Row and Column-Level Restrictions: Restrict queries to authorized data segments.
- Fine-Grained Field Permissions: Protect confidential fields while enabling analytical workflows.
By restricting compute access appropriately, analysts can perform required analyzes without compromising sensitive data, ensuring both operational efficiency and compliance.
5. Enabling Secure Collaboration and Compliance
RBAC strengthens both security and operational governance in Microsoft Fabric:
- Access Control: Users and services can only access data and resources they are authorized to use.
- Compliance: Aligns with regulatory requirements including GDPR, HIPAA, and industry-specific standards.
- Collaboration Efficiency: Teams can focus on business-critical work without risking sensitive information.
6. Scaling Security and Governance for Enterprise Workloads
RBAC in Microsoft Fabric is designed to scale with enterprise demands, supporting growing teams and complex operations:
- Role Hierarchies: Simplify permission management across large organizations.
- Automation-Friendly Access: Integrate service principals to enable secure automated workflows.
- Granular Security Policies: Apply permissions consistently across workspaces, assets, and compute resources.
This flexible framework ensures enterprises can maintain security, compliance, and productivity while scaling their Microsoft Fabric deployments efficiently.
Also Read: Guide to Data Security and Privacy in Microsoft Fabric
With access properly managed across workspaces, items, service principals, and compute, it’s important to understand the tangible business benefits RBAC delivers.
How Does Role-Based Access Control Fabric Impact Businesses?
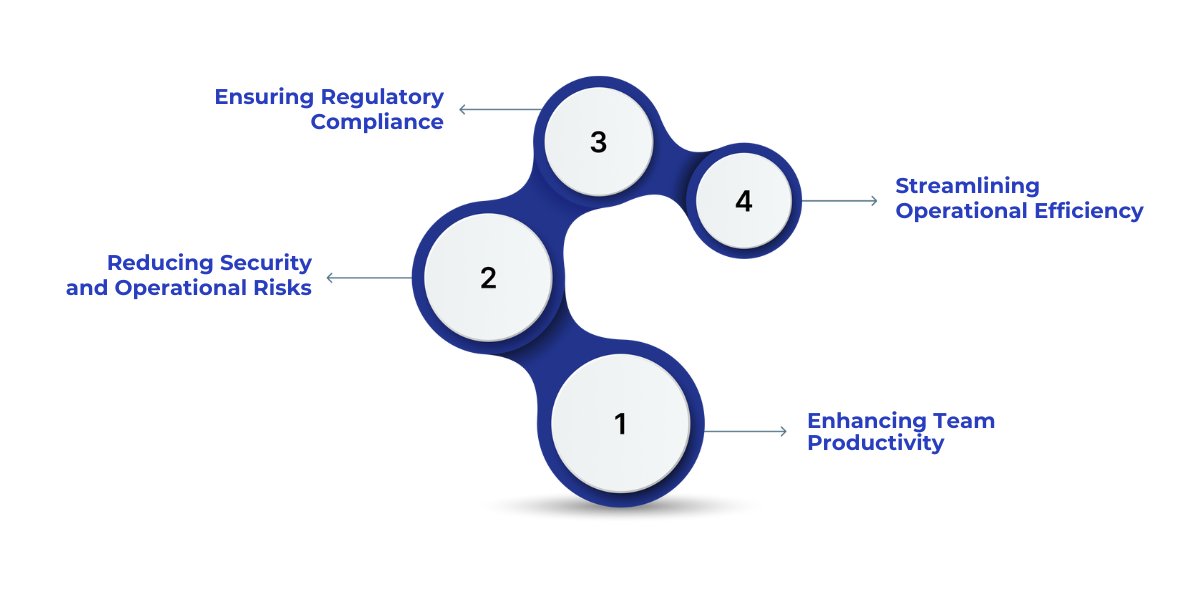
Role-Based Access Control (RBAC) in Microsoft Fabric is more than a security feature, it actively supports business performance by aligning access with organizational responsibilities.
Proper implementation enables enterprises to protect sensitive data while improving productivity, efficiency, and compliance.
Here’s how RBAC drives productivity, reduces risk, and ensures compliance:
1. Enhancing Team Productivity
Effective RBAC implementation begins with ensuring that teams can access the resources they need without unnecessary delays. By clearly defining permissions, organizations enable employees to focus on their core responsibilities and streamline workflows:
- Targeted Access: Team members can work efficiently because they only access resources relevant to their roles.
- Faster Decision-Making: Streamlined permissions reduce bottlenecks, allowing faster execution of projects and analytics workflows.
2. Reducing Security and Operational Risks
In addition to improving productivity, RBAC safeguards businesses from the risks of overexposed or mismanaged Fabric data integration. By restricting access according to roles, enterprises can reduce security incidents and operational errors:
- Controlled Permissions: Sensitive datasets, reports, and pipelines are protected from unauthorized changes.
- Error Reduction: Limiting write access minimizes accidental modifications that could disrupt analytics or business operations.
3. Ensuring Regulatory Compliance
Another critical benefit of RBAC is its ability to simplify compliance. By enforcing consistent policies across teams, organizations can meet regulatory requirements with ease:
- Policy Enforcement: Access rules are consistently applied across all workspaces and items.
- Simplified Audits: Clear role structures make compliance checks more straightforward and less time-consuming.
4. Streamlining Operational Efficiency
Finally, RBAC improves operational efficiency by reducing administrative overhead. Automated and clearly structured access controls allow IT teams to manage permissions efficiently and focus on higher-value tasks:
- Clear Role Definitions: Predefined roles like Admin, Member, Contributor, and Viewer align responsibilities with permissions.
- Simplified Administration: Regular reviews and automated provisioning help IT teams manage access efficiently.
Also Read: Microsoft Synapse vs Fabric: Comprehensive Comparison
With business benefits clear, enterprises must also understand common implementation challenges, which we explore next.
RBAC Challenges and Best Practices in Microsoft Fabric
Enterprises often face hurdles like overprovisioned access, shadow IT, and scalability issues when implementing RBAC. Microsoft Fabric provides a secure and flexible platform to manage access at scale.
Before implementing RBAC, it’s important to anticipate potential challenges and understand how to address them effectively.
The following table summarizes common obstacles and practical solutions for maximizing security and efficiency:
By proactively addressing these challenges, enterprises can ensure RBAC delivers both security and scalability, supporting seamless collaboration across teams.
As RBAC matures, emerging trends are set to redefine security and collaboration in Fabric, let’s explore that next.
Future Trends and Implications for RBAC in Microsoft Fabric
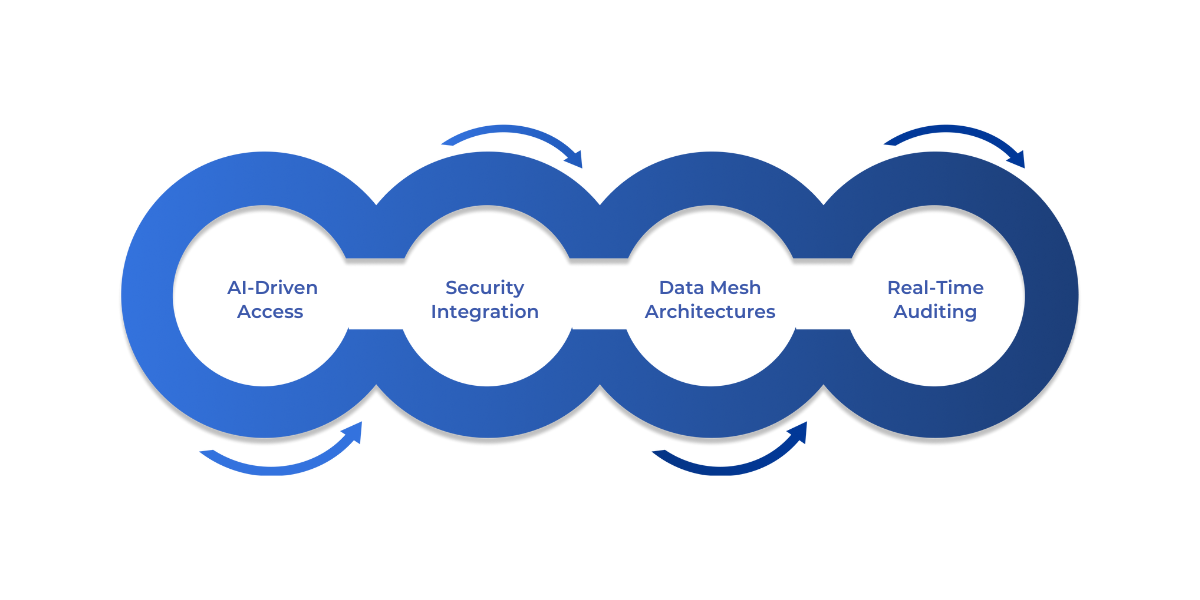
As enterprises expand their data ecosystems, Role-Based Access Control (RBAC) will play a more critical role in balancing security, governance, and collaboration within Microsoft Fabric. Its continued evolution will shape how organizations protect sensitive data while enabling productivity.
Some emerging trends include:
- AI-Driven Access Management: Machine learning models will automatically adjust roles and permissions based on user behavior, reducing manual oversight and strengthening proactive security with AI integration.
- Zero Trust Security Integration: RBAC will work alongside zero trust principles, enforcing continuous authentication and verification rather than relying solely on predefined roles.
- Alignment with Data Mesh Architectures: As enterprises adopt decentralized data ownership, RBAC will integrate more closely with data mesh models, ensuring scalable and federated governance.
- Real-Time Auditing and Monitoring: Continuous auditing capabilities will provide real-time analytics and visibility into access patterns, enabling quicker detection of anomalies and stronger compliance management.
These advancements will ensure RBAC in Microsoft Fabric remains adaptive, scalable, and future-ready for enterprise needs.
Conclusion
Role-Based Access Control (RBAC) in Microsoft Fabric offers enterprises a secure way to manage access, protect sensitive data, and maintain compliance while supporting collaboration.
As organizations scale their analytics and data-driven operations, RBAC becomes essential for balancing security with productivity.
That said, the effectiveness of RBAC depends on the right implementation and ongoing governance. Enterprises must align role definitions, monitor permissions, and adapt access policies to evolving business needs.
At WaferWire, we help businesses design, implement, and optimize RBAC strategies within Microsoft Fabric.
Contact us today to strengthen your Fabric environment with secure, scalable, and well-governed access control.
FAQs
1. What is Role-Based Access Control (RBAC) in Microsoft Fabric?
RBAC assigns permissions based on roles rather than individual users, ensuring secure, role-aligned access that reduces risk and streamlines collaboration.
2. How does RBAC improve security in Microsoft Fabric?
It prevents unauthorized access, limits exposure to sensitive data, and enforces consistent governance across workspaces, items, and compute environments.
3. Can RBAC be applied at both workspace and item levels?
Yes, Microsoft Fabric allows role-based permissions at both workspace and item levels, offering flexibility and granular control for enterprise data management.
4. How does RBAC support compliance requirements?
By controlling access to sensitive information, RBAC helps enterprises meet regulatory standards like GDPR, HIPAA, and SOC 2 with stronger governance practices.
5. What’s the difference between RBAC and attribute-based access control (ABAC)
RBAC grants access based on defined roles, while ABAC uses attributes such as department or location for finer control. Many enterprises adopt a hybrid model for flexibility.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)














