Building a Successful Data Security Protection Strategy: Best Practices
Mitra P
2025-03-07

Talk to our cloud experts
Subject tags
With cyber threats escalating at an alarming rate, businesses must prioritize data protection like never before. From ransomware attacks to insider threats, the risks are growing more sophisticated, making implementing data security best practices that go beyond traditional defenses is essential. A well-structured data security strategy ensures compliance with industry regulations and safeguards sensitive information from unauthorized access, breaches, and data loss.
In this guide, we’ll explore the critical pillars of data security to help organizations build a robust security framework.
Data Security Protection Strategy
A data security strategy is a comprehensive plan designed to protect an organization’s information assets from unauthorized access, disclosure, alteration, and destruction. Its primary objectives include ensuring data confidentiality, integrity, and availability. This involves implementing measures to prevent data breaches, detect potential threats, and respond effectively to security incidents.
Differentiation from Data Protection Strategy
While often used interchangeably, data security and data protection strategies serve distinct purposes. Data security focuses on safeguarding data against malicious threats and breaches through technical measures like encryption, access controls, and network security. In contrast, data protection encompasses a broader scope, including policies and procedures to ensure data privacy, compliance with legal regulations, and proper data handling throughout its lifecycle.
Focus Areas: Access Control, Data Security, and Data Availability
- Access Control: Implementing strict access controls ensures that only authorized personnel can access sensitive data. This includes using strong passwords, multi-factor authentication, and role-based access controls to limit data access based on an individual’s organizational role.
- Data Security: Employing measures such as encryption, firewalls, and intrusion detection systems to protect data from external and internal threats. Regular security assessments and updates are crucial to address emerging vulnerabilities.
- Data Availability: Ensuring that data is accessible to authorized users when needed. This involves regular data backups, disaster recovery planning, and maintaining redundant systems to prevent data loss from hardware failures or cyber attacks.
Transitioning from understanding the foundational elements, let’s delve into the key components of a data security protection strategy to effectively safeguard your organization's data assets.
Key Components of a Data Security Protection Strategy

Data breaches are costly. Beyond financial losses, they erode customer trust and put businesses at legal risk. A strong data security protection strategy is non-negotiable for enterprises and mid-market companies. Let’s break down the core components every business must prioritize to maintain security without disrupting operations.
1. Data Access Management and Controls
Controlling who accesses data and how is the foundation of security. A compromised account can expose confidential information, damaging reputational and financial damage.
- Role-Based Access Control (RBAC): Employees should only access data essential to their role. For example, a financial analyst doesn't need access to HR records.
- Multi-Factor Authentication (MFA): Passwords alone are not enough. Adding a second layer of verification, such as a one-time passcode or biometric authentication, reduces the risk of breaches.
- Identity and Access Management (IAM): Automates user access and ensures ex-employees or unauthorized users lose access immediately.
2. Data Encryption
Even if a hacker gets hold of sensitive information, encryption makes it unreadable. This applies to data stored on servers, transferred between systems, or accessed remotely.
- Data at Rest: Protects stored data using encryption standards like AES-256.
- Data in Transit: Encrypts data when it’s being sent over the internet or internal networks. TLS and VPNs secure these transfers.
- End-to-End Encryption (E2EE): Ensures only intended recipients can access messages or files.
3. Data Backup and Recovery
Cyberattacks, hardware failures, and natural disasters can wipe out data in seconds. A robust backup and recovery plan ensures businesses can restore critical information quickly.
- Automated Backups: Regularly scheduled backups prevent data loss from ransomware or accidental deletion.
- Offsite and Cloud Backups: On-premises backups aren’t enough. Cloud backups ensure data remains accessible even if physical servers are compromised.
- Disaster Recovery Plan: A structured recovery process minimizes downtime and keeps operations running.
4. Data Storage Management
Where and how businesses store data affects both security and compliance. A well-managed storage system reduces risks and improves accessibility.
- Secure Transfers: Files moving between on-premises, cloud, and hybrid systems must be encrypted and monitored.
- Hybrid and Cloud Storage Security: Businesses using Microsoft Azure, or Google Cloud must enable built-in security features, including encryption and access controls.
- Regular Audits: Detect unauthorized access or storage misconfigurations before they become a problem.
Beyond security components putting them into action is where businesses gain real protection. Next, we explore how to implement strong data security best practices to safeguard critical information effectively.
Implementing Strong Data Security Best Practices
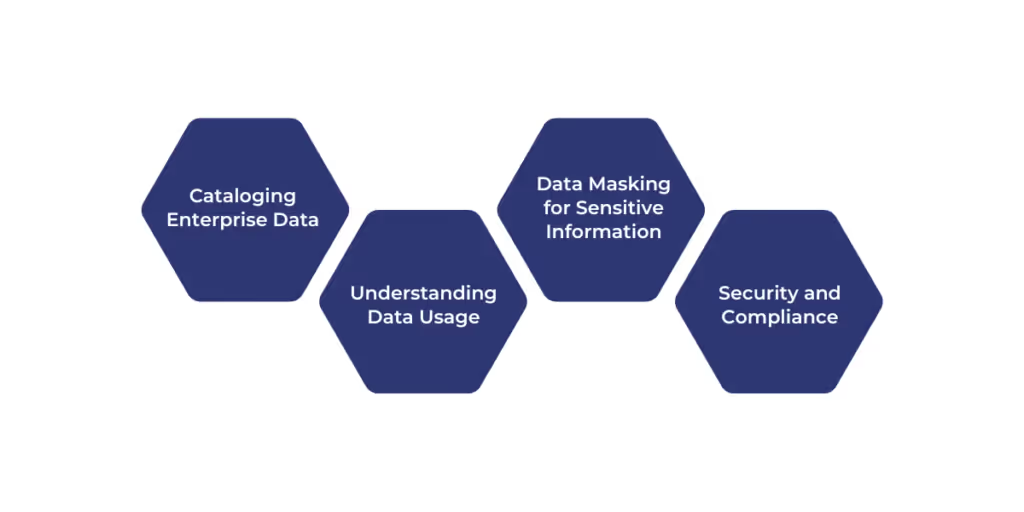
To implement data security best practices, businesses must focus on visibility, control, and awareness at every stage of data handling.
Cataloging Enterprise Data
One of the biggest challenges companies face is not knowing where their data is stored or how it moves across different systems. Without proper inventory, securing critical information becomes nearly impossible.
The first step is identifying all data sources, including databases, cloud storage, internal files, and third-party applications. After mapping, data should be categorized according to sensitivity; operational data is less secure than financial records, customer information, and intellectual property.
Data ownership must also be defined. Assigning responsibility ensures access control, compliance, and policy enforcement. Without accountability, sensitive information can easily be mismanaged.
Understanding Data Usage
Having a clear view of how employees and third parties access and use data is essential for preventing security breaches. Many organizations face insider threats, whether intentional or accidental, simply because there are no clear restrictions on data access. Strong access control policies ensure only authorized personnel can view or modify sensitive data.
Role-based access control (RBAC) should be implemented to limit data access according to job responsibilities. User activity must also be monitored in real time. Unusual access patterns, such as an employee downloading large volumes of data or logging in from an unfamiliar location, should trigger alerts and immediate action. When an American retail company suffered a data breach, investigations revealed that a former vendor had accessed sensitive pricing details using old credentials. The breach wouldn’t have happened if access had been automatically revoked after the vendor contract ended.
Data Masking for Sensitive Information
Sensitive data is often used for testing, analytics, and development, but exposing real customer or financial information in these environments creates unnecessary risks. Data masking ensures that sensitive details are hidden or replaced while keeping datasets functional.
One way to achieve is through dynamic masking, which alters data based on user access levels. If an unauthorized user attempts to access restricted information, they only see scrambled or anonymized data instead of the actual content. Static masking, on the other hand, is useful for test environments. Before sharing data with third parties or using it for internal testing, sensitive details should be permanently replaced with fictitious values to prevent accidental leaks.
Tokenization is another effective method. This replaces real data with randomized tokens that have no meaningful value unless decrypted with the right security key.
Security Awareness Training for Employees
Technology alone cannot prevent data breaches if employees are unaware of the risks. Many cyberattacks happen due to human error, such as weak passwords, phishing scams, or mishandling sensitive files. Without proper training, even the best security tools can be bypassed.
Every employee must be trained to recognize phishing attempts. Attackers often disguise themselves as trusted contacts, sending fraudulent emails designed to trick recipients into revealing login credentials or downloading malware. Running regular phishing simulations helps staff identify these threats and respond correctly.
Social engineering tactics also pose a significant risk. Cybercriminals manipulate employees into granting access to confidential data by pretending to be a trusted colleague or vendor. Training sessions should include real-life examples of how these attacks occur and how to verify requests before taking action.
Beyond individual training, organizations must establish clear security policies. Employees should understand what data they can share, how files should be stored securely, and how to report suspicious activity. Without documented guidelines, security awareness remains inconsistent, leaving businesses vulnerable to preventable breaches.
Strong security practices lay the foundation. However, advanced security technologies like AI-driven threat detection, endpoint protection, and automated compliance monitoring take security to the next level. Let’s explore how technology enhances data security best practices for modern enterprises.
Using Advanced Security Technologies
Advanced security technologies enhance prevention and response, ensuring businesses can detect risks early, block potential threats, and maintain uninterrupted operations.
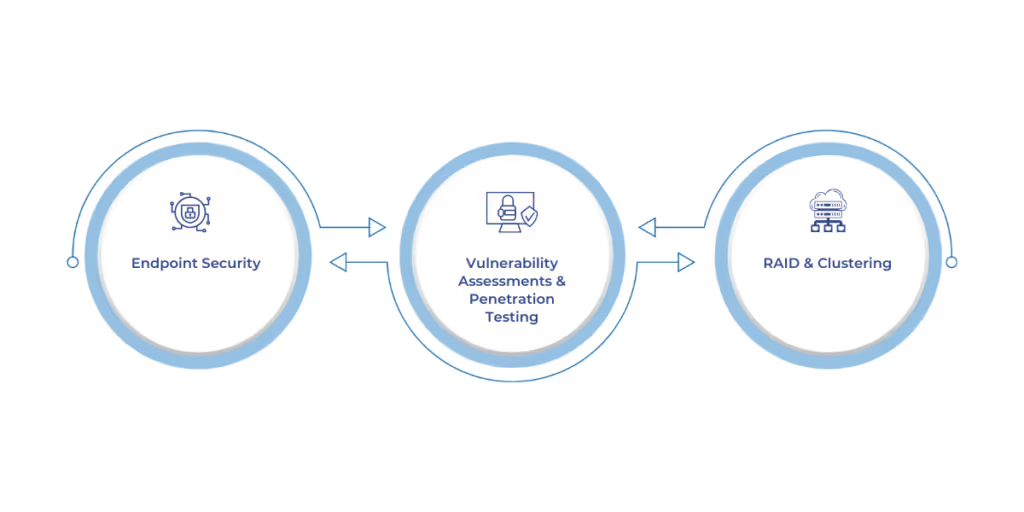
Endpoint Security
Every laptop, server, and mobile device connected to a network is a potential entry point for cybercriminals. If just one endpoint is compromised, attackers can access critical systems, steal data, or launch ransomware attacks.
Comprehensive endpoint security includes:
- Next-gen antivirus solutions that detect and block malware before it executes.
- Endpoint Detection and Response (EDR) tools analyze real-time behavior to flag suspicious activity.
- Intrusion Detection Systems (IDS) that monitor network traffic for unauthorized access attempts.
Vulnerability Assessments & Penetration Testing
Many cyberattacks succeed because businesses aren’t aware of their weakest security points. Hackers exploit outdated software, misconfigured systems, and weak credentials to gain unauthorized access.
To stay ahead, businesses must conduct regular security evaluations.
- Vulnerability assessments scan for outdated software, weak configurations, and missing patches.
- Penetration testing simulates real-world cyberattacks, exposing system weaknesses before criminals do.
RAID & Clustering
Security is also about ensuring that data remains accessible even in the event of system failures. Hardware malfunctions, cyber incidents, and power outages can all disrupt business operations.
RAID (Redundant Array of Independent Disks) and clustering technologies ensure businesses can recover quickly without data loss.
- RAID distributes data across multiple hard drives. If one fails, the system keeps running.
- Clustering allows multiple servers to work together, balancing workloads and ensuring uptime.
Without clear security policies, even the most advanced tools can be ineffective. The next step is to establish strong data security policies and procedures.
Establishing Data Security Policies and Procedures
Technology alone cannot safeguard against data leaks and compliance risks; robust policies are essential. Clear rules on classification, storage, and security ensure businesses stay protected, operational, and trusted.
Defining Data Classification
Not all data is created equal. Some information like financial records, customer details, and intellectual property requires strict security controls. Other data, such as general operational reports, may not need the same level of protection.
A structured classification system is essential. Businesses must determine:
- What data is considered sensitive?
- Who can access it?
- How should it be stored and protected?
Many companies make the mistake of treating all data the same. This leads to security fatigue, where unnecessary restrictions slow down operations, and real threats go unnoticed.
Data Collection and Retention
Data retention poses a security and legal risk in addition to being a matter of storage capacity. Numerous breaches reveal outdated, superfluous data that ought to have been removed. Companies need to set up explicit retention guidelines that specify:
- What data needs to be stored?
- For how long?
- When should it be deleted or archived?
Regulatory compliance also plays a role. Industries like healthcare and finance have strict retention rules. Non-compliance can result in massive fines and reputational damage.
Incident Response Plans
No security system is perfect. Even the best-prepared companies are vulnerable to cyberattacks, insider threats, and data breaches. How quickly a business detects, contains, and responds to the incident often determines whether it is a minor security event or a catastrophic breach.
An effective Incident Response Plan (IRP) ensures that security teams:
- Know the warning signs of an attack.
- Have a predefined escalation process.
- Communicate breaches to customers and regulatory bodies when necessary.
Even the best policies can’t prevent insider threats and compliance violations without active enforcement. In the following section, we will examine how companies can identify and reduce internal security threats while adhering to changing legal requirements.
Addressing Insider Threats and Compliance
Insider threats pose a significant risk as employees, vendors, or contractors may misuse access, either intentionally or unintentionally. Unrestricted access, poor monitoring, and a lack of security policies increase the chances of data leaks or fraud. Strict access control, continuous monitoring, and automated access revocation are essential to prevent unauthorized activity.
Compliance with GDPR, CCPA, and industry-specific regulations requires businesses to protect personal data, report breaches promptly, and enforce strict data governance. Failure to comply results in financial penalties and legal consequences. Regular audits, employee training, and automated enforcement ensure ongoing compliance.
Companies must use risk assessment and ongoing monitoring to identify threats and take immediate action. The next discussion will be how continuous security monitoring improves data security.
Read more: https://waferwire.com/blog/key-principles-scalable-architecture/
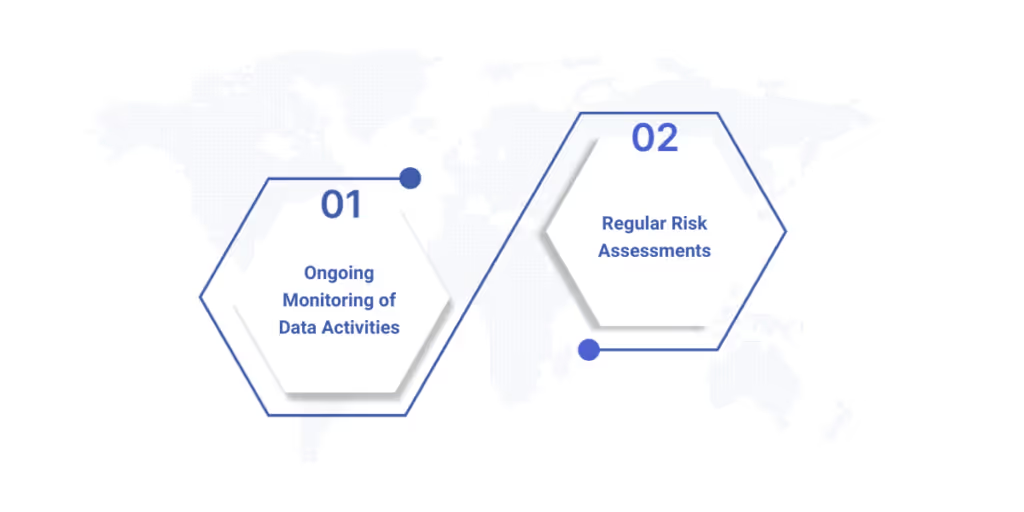
Continuous Monitoring and Risk Management
Cyber threats are unpredictable, so businesses must actively track data activity and assess risks to prevent security breaches. A strong monitoring strategy helps detect unauthorized access.
Ongoing Monitoring of Data Activities
Security teams must have real-time visibility into who accesses data, how it is used, and where it is stored. Unauthorized data transfers or login attempts must be flagged immediately. Monitoring systems should track file movements, detect anomalies, and trigger automated alerts when suspicious activity occurs. Without continuous oversight, businesses may not recognize a breach until critical information is lost.
Regular Risk Assessments
Security risks evolve as systems expand and cybercriminals adapt. Frequent risk assessments help businesses uncover weaknesses and strengthen security policies. This includes evaluating access controls, vendor security, and potential compliance gaps. Reviewing and updating policies based on new threats ensures that security frameworks remain effective.
Conclusion
Cyber threats don’t wait, and neither should businesses. A static security strategy is a ticking time bomb. Data security best practices demand constant evolution, real-time monitoring, and proactive risk management. Anything less leaves organizations vulnerable—not just to cyberattacks but to financial penalties, operational disruptions, and irreversible damage to customer trust.
Organizations that fail to prioritize security will fall behind, facing compliance violations and preventable breaches. The difference between a company that thrives and one that suffers a catastrophic data loss comes down to preparation. The right strategy does more than just reduce risks; it provides organizations the confidence to innovate and scale without fear.
This is where WaferWire delivers a competitive edge. From strategy to execution, we empower enterprises and mid-market businesses with robust security solutions that ensure compliance, threat detection, and long-term resilience.
The question isn’t whether you need better security; it’s whether you’re ready to take action. Get in touch with us today and take control of your data security in the future.
Subscribe to Our Newsletter
Get instant updates in your email without missing any news

Copyright © 2025 WaferWire Cloud Technologies




.png)